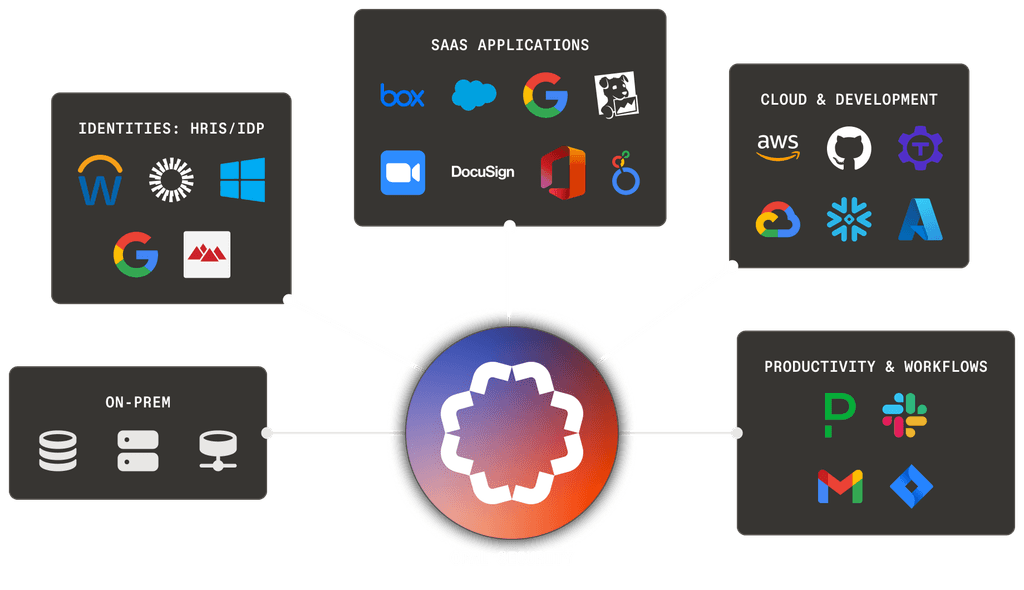
Access Management Integrations
Depth Matters.
Achieving least privilege access requires more than just surface-level integrations—it demands precision, depth, and actionable control across your most critical systems. Opal’s industry-leading, first-party read/write integrations enable fast and safe identity risk reduction.
Jump to catalog
Integrations with key identity sources such as IDP, HRIS, Google Workspace quickly sync identities and allow for a fast deployment and short time to value.



Deep, granular integrations with cloud environments, development platforms, and data systems ensure that your most valuable assets are protected with unparalleled accuracy.
First-party integrations with dozens of the most popular B2B SaaS applications enable fast protection of the apps that contain your most sensitive data.




For all other resources, including internal apps, custom connectors empower you to seamlessly integrate with any SaaS, cloud, or on-premises system.
Productivity connectors streamline access requests and management through tools like Slack, automated PagerDuty schedules, and more.



Integration Catalog

Active Directory
Identity
Amazon Aurora
Databases

Amazon Web Services (AWS)
Cloud
Amazon EC2
Compute

Amazon EKS
Compute

AWS IAM Role
Cloud

AWS SSO / IAM Identity Center
Cloud

Azure Blob Storage
Cloud

Azure SQL
Databases

Azure VM
Compute

Databricks
Databases

Duo
Applications

Applications

Entra ID
Identity

GCP Bucket
Cloud

GCP Cloud SQL
Databases

GCP Compute
Compute

GCP Folder
Cloud

GCP GKE
Compute

GCP Project
Cloud

GitHub
Source Control

GitLab
Source Control

Google Chat
Communication

Google Cloud Platform (GCP)
Cloud

Google Groups
Identity

Google Workspace
Applications

Internal Tools
Applications

Jira
Help Desk

LDAP
Identity

Linear
Help Desk

MongoDB
Databases
MySQL
Databases
Okta
Identity

Opsgenie
On-Call

PagerDuty
On-Call

Postgres
Databases

Salesforce
Applications

ServiceNow
Help Desk

Slack
Communication

Snowflake
Databases
Tailscale
Databases

Teleport
Cloud

Terraform
Cloud

Twingate
Cloud

Workday