Jun 6, 2023
•
Product
Custom App Integration
Customer Context
Technology companies have created internal tools to help their support staff serve customers at scale. These internal tools can be incredibly powerful and are often used by a wide array of employees, ranging from full-time to contractors. Given the breadth of the attack surface and the sensitivity of data, internal tools are often targets for breaches. In 2022, the notorious cybercriminal group Lapsus$ got ahold of Okta’s internal admin console through a compromised customer support representative.
Breaches are incredibly difficult to prevent. With the evolving threat landscape, enterprises are playing a never-ending cat-and-mouse game. Increasingly, organizations are focusing more on threat reduction by minimizing the amount of privileges granted. While this seems straightforward in practice, the realities of implementation are difficult. Productivity and security are often seen as mutually exclusive. Overly restrictive processes can grind businesses to a halt.
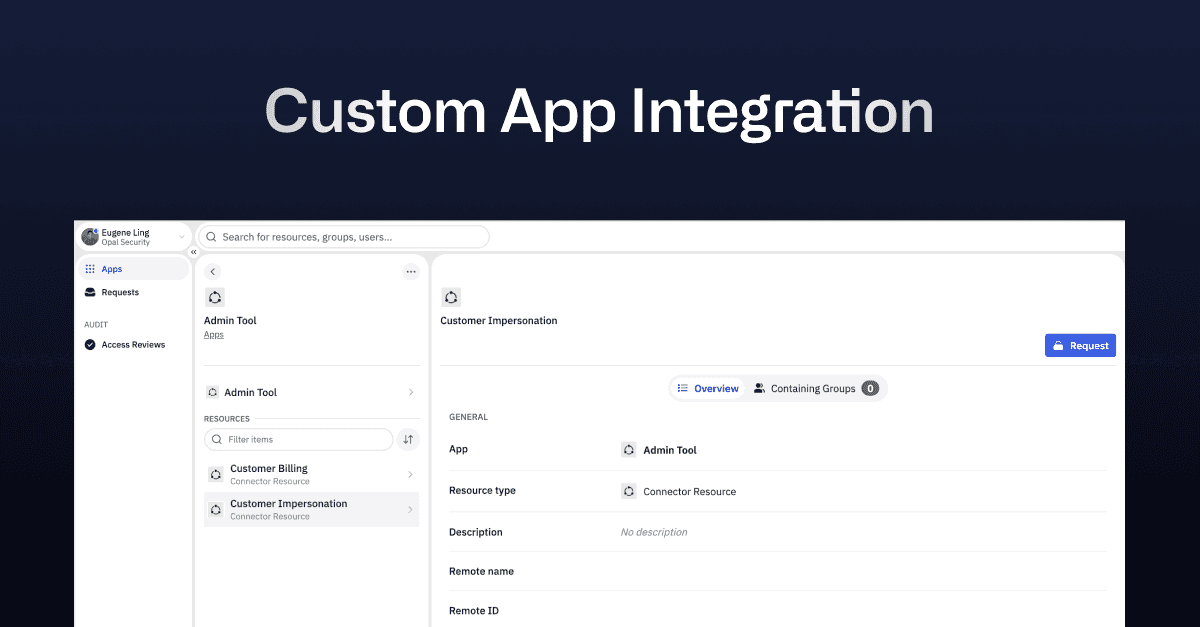
With Opal’s custom app integration, enterprises can implement just-in-time access for internal applications – enabling employees to request for specific and time-bounded permissions easily through Slack or Opal. Ultimately, this allows Opal to help increase the security posture of highly privileged internal tools with a simple and delightful user experience.
Customer Value
We wrote an article outlining how we use Opal to manage our internal impersonation tool. As a quick summary, we use Opal internally for:
Just-in-time access: Employees do not have long-standing access, and requests are just-in-time and fully audited

Granular access: Access to the internal tool is highly scoped using access levels

Time-bounded access: All access to the internal tool will automatically expire

Authenticated approvals: Approvers must validate their identity using 2FA

Audited controls: All approvals are audited

About Opal
Opal is the unified identity platform for modern enterprises. Opal aggregates identity and access data to provide visibility and defense-in-depth infrastructure for mission-critical systems. Enterprises can discover anomalous identity risks with the product and remediate them in minutes. The world's best companies trust Opal to govern and adapt sensitive access.
Want to see it yourself? Contact sales@opal.dev or book a meeting here for a personalized demo.