Jun 3, 2024
•
Product
Introducing Group Optimization: Reducing Group-Based Identity Risk With Precision
The Challenge
Access and authorization are often managed through groups, with role or attribute based factors determining which people are in which groups, and which resources those groups have access to. However, over time, individual roles can change, as can group responsibilities. Groups can also be blunt instruments - for example a group for a development team could include individuals such as doc writers, testers, etc that do not need the same resources as coders. In all of these cases, the result can be significantly over-provisioned access - either by including users in a group that do not need nor use certain resources, or by providing the entire group with access to resources or permissions they do not need or use. This type of access sprawl was noted by Gartner, who found that more than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted.
What is Group Optimization?
Group Optimization is a new feature enhancing Opal’s recently launched Least Privilege Posture Management capability. It enables customers to identify groups that are overprovisioned, prioritize that access risk against other findings to enable focus, and remediate the issue quickly.
The feature covers two forms of over-provisioned group access or authorization:
It identifies users in a group - such as an Okta or Google group - that have not leveraged that group to access any of its assigned resources for over 30 days.
It identifies resources allocated to a group that none of the group members have accessed within 30 days.
In both cases, this is an indication of overprovisioning - either of users to the group or the group to certain resources.
These findings are prioritized against other identity risk issues identified by Opal’s platform leveraging multiple risk factors. For example, groups with unused access to a sensitive resource would be a higher priority than groups with unused access to a resource not deemed to be sensitive. This enables teams to focus their remediation efforts fixing the issues that will have the greatest impact on risk reduction.
For each group risk identified, Opal enables fast remediation. In just a couple of clicks, IAM or security teams can remove users from groups they are not leveraging, remove resources from groups that are not being used, or convert access to Just-In-Time (JIT) with an expiration date for access.
Key Benefits
Manage Least Privilege Posture: The core tenant of Least Privilege is providing only the access and privileges needed to do the job, and only for the time required to do the job. By identifying and removing users in groups, and groups that in total. that are not leveraging resources, security and IAM teams can quickly improve the Least Privilege posture of their organization.
Reduce Risk: Revoking users and groups, or converting them to JIT access, shrinks the overall attack surface and reduces the risk of breach without impacting employee productivity or the business’ ability to function and grow.
Reduce IT Costs: By revoking unused access, companies are able to save on licensing costs for applications that license by user.
How It Works
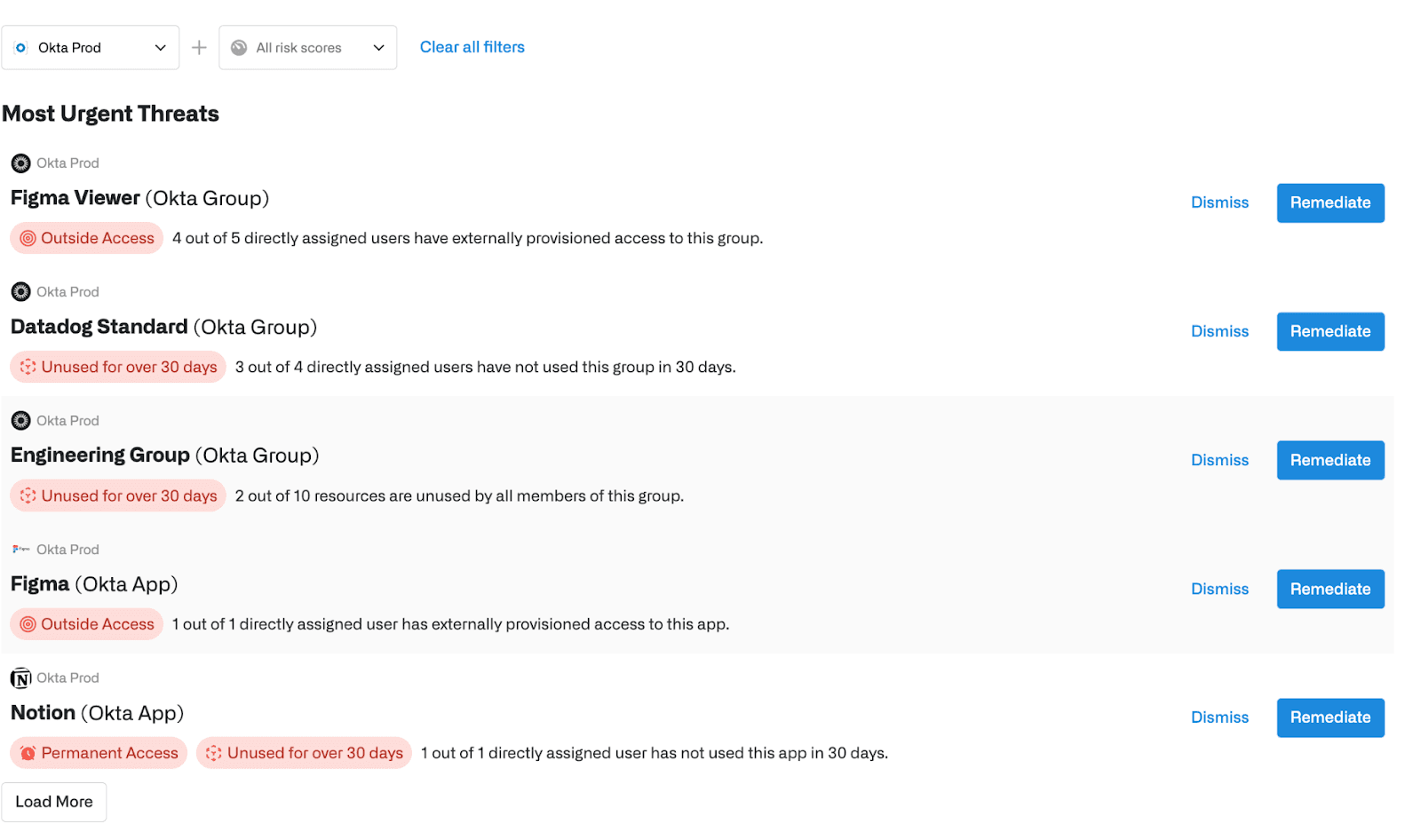
In Opal’s Least Privilege Posture Management Risk View, over-provisioned group access is now displayed and prioritized. In this example (below), we see that 3 out of 4 users in the ‘Datadog Standard’ group have not used the group in over 30 days. We also see that no one in the ‘Engineering Group’ has leveraged 2 out of the 10 resources available to this group for over 30 days.
The administrator - typically a member of the security team or an IAM owner - can choose to either dismiss the warning, or if they want to address it, can click to ‘Remediate’.
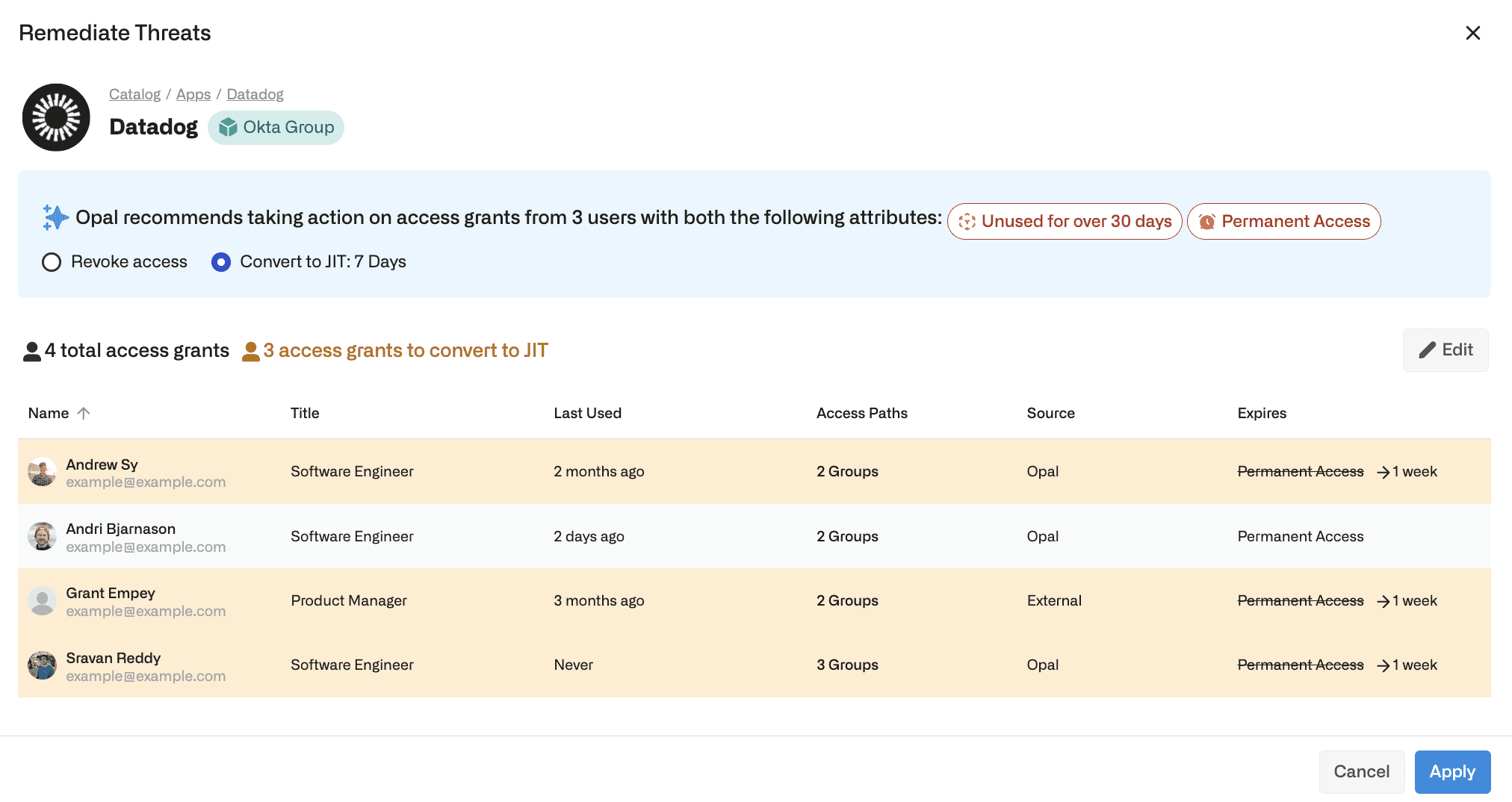
Remediating the ‘Datadog’ group consists of either revoking user access to the group, or converting access to JIT with a 7 day expiration. If needed, further granularity can be accessed by using the ‘Edit’ button, enabling different actions for individual users or different durations for the JIT access. Upon clicking ‘Apply’, Opal leverages write access to make the change in the relevant system (in this instance in Okta).
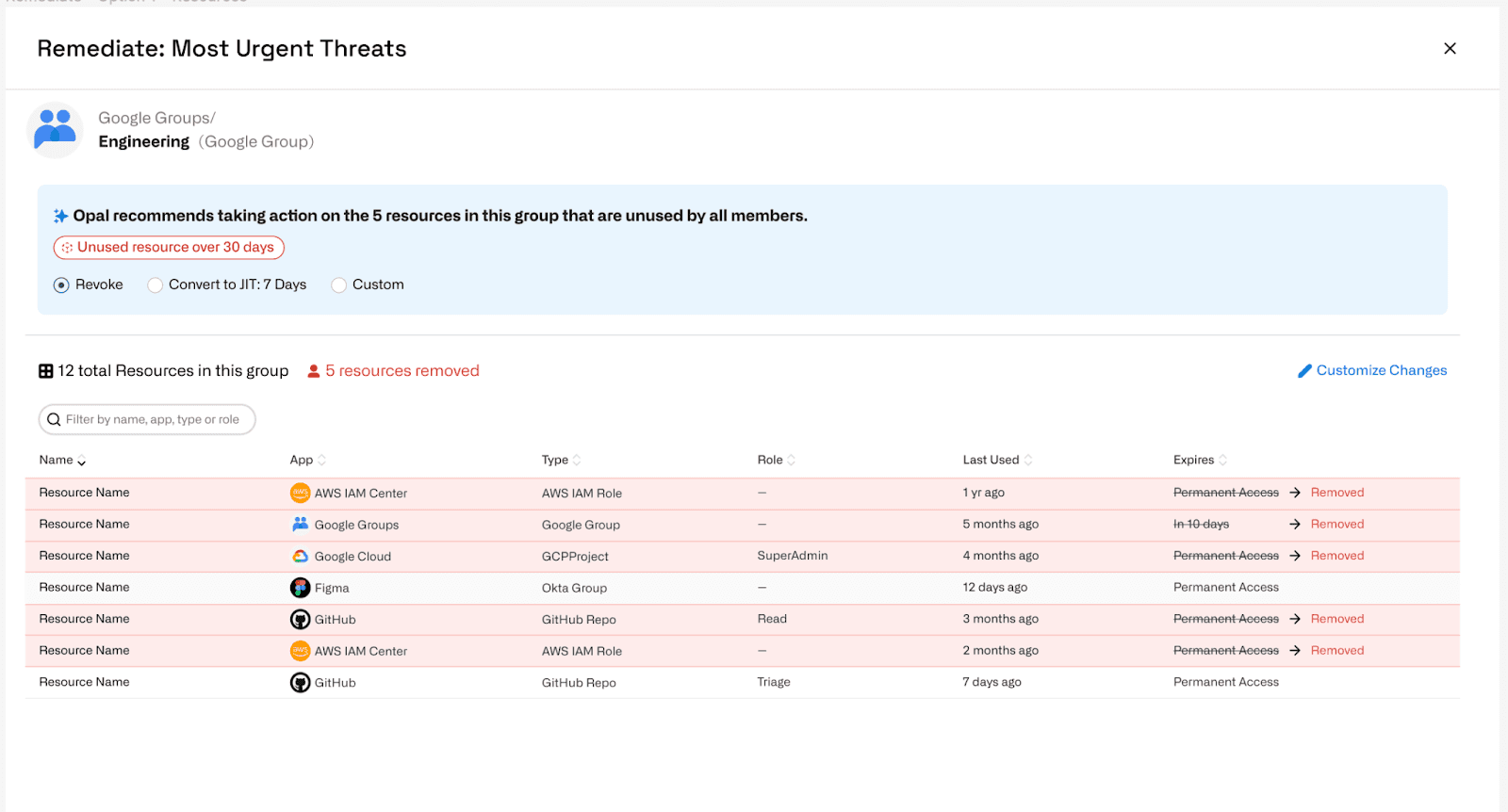
Remediating the ‘Engineering’ group consists of revoking group access to unused resources or converting to JIT. As with users, these options can be configured more granularly if desired, and completing the action will make the change instantly.
How to Use Group Optimization
The Group Optimization feature is available in beta for all Opal Security customers. Interested customers can contact their Technical Account Manager to enable this feature.
About Opal Security
Opal Security is redefining identity security for modern enterprises. The unified platform aggregates identity and access data to provide customers with visibility and rapid control to protect mission-critical systems while accommodating the complexity and agility businesses require for growth. IT and security teams can discover anomalous identity risks and remediate them in minutes. Many global leaders, including Databricks, Figma and Scale AI, trust Opal Security to enable them to govern and adapt sensitive access quickly and securely.


