May 16, 2024
•
Product
Introducing Group Projects: Managing Access for Temporary Groups with Opal Security
The Challenge
Access and authorization to critical systems are usually requested and granted on an individual basis. This process can be based on birthright policies, role or attribute-based controls, or individual requests for time-bound access (JIT).
However, some of our customers faced a challenge when assembling teams for temporary projects, such as an urgent product update. In these cases, an individual request would need to be made for each person on the team. In these cases, each team member must request access individually for each needed resource. Alternatively, a project leader could request on each team member’s behalf, but they would have to separately request access for each person for each resource that was needed. This process is time-consuming, especially for cross-functional and temporary teams not already grouped in an IDP or identified in the HR system. These individual requests take a lot of time, which may be scarce during an urgent project. This workflow also risks access sprawl, as it is time consuming to revoke all of the individual access after the project is complete, and that step might be skipped. Gartner noted that 90% of accounts use less than 3% of the entitlements they are granted - and these temporary project situations can be contributors to that problem.
What is Group Projects?
The Group Projects feature enables a user with a new Opal role called ‘Project Leader’ to create a group, add people to it, and then request access to all resources needed on behalf of the group. Whoever owns the approval for accessing each resource can approve the group as a whole, making it faster and easier for them to provide access to the team. When the access is approved, it grants access to all the people in the group at once.
As with all other requests Opal supports, time-bound access is easily granted, ensuring it will revoke automatically after a set duration. The project leader can also delete the group at any time (for example, at the end of the project, or if the project was canceled) instantly revoking all granted access.
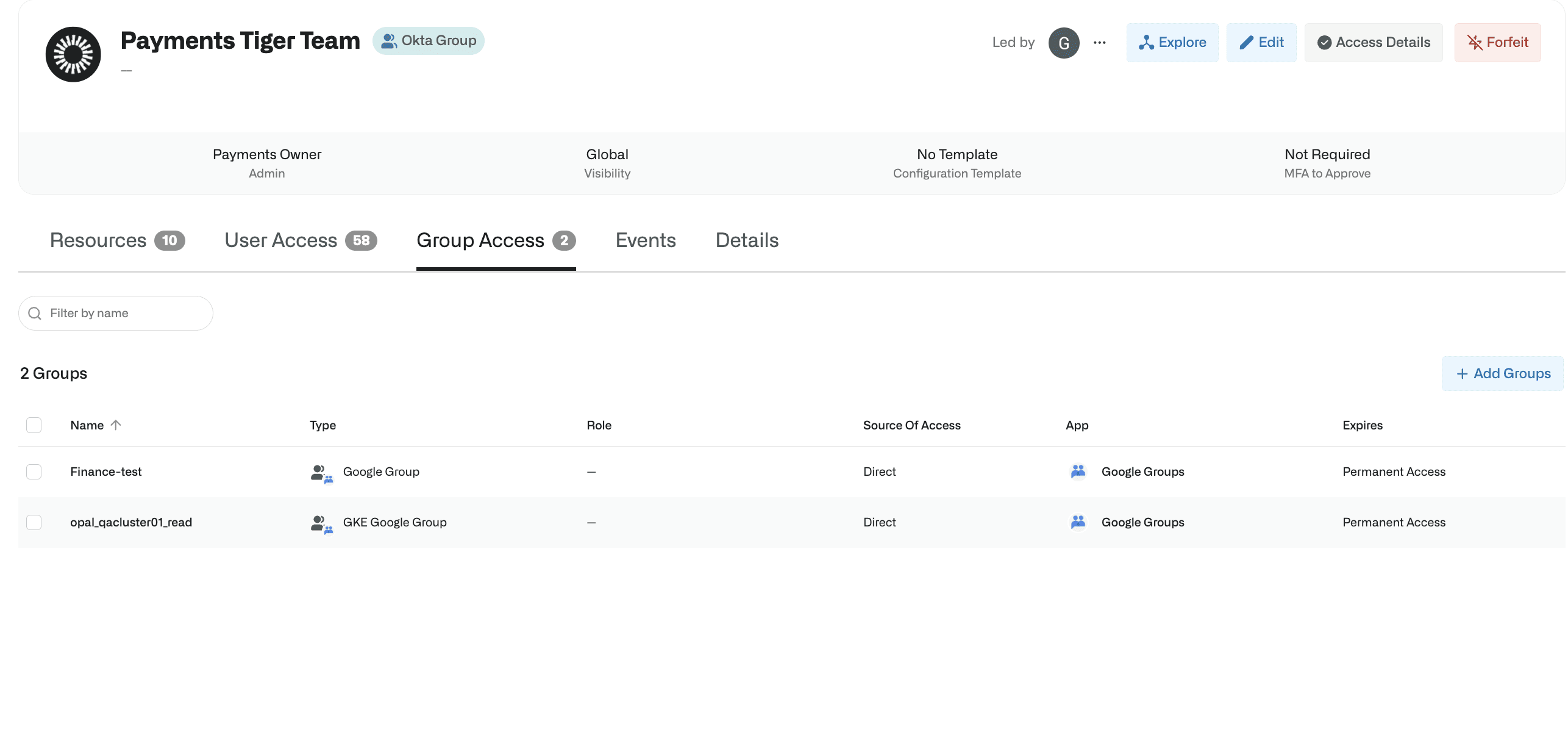
As some projects can require pre-existing groups to be granted access or privileges, the Group Projects feature enables nesting of groups - so project groups can include both individual users and/or other groups. This can be especially helpful to quickly bring in groups defined in other system architectures, such as Okta groups or Google groups, or to grant access to groups of people to multiple Okta groups.
As with most things in Opal, Project groups can be managed either in the UI or using the Opal API, enabling automation.
Key Benefits
Save Time: Streamlines the process of requesting and granting access for temporary projects.
Reduce Risk: Simplifies temporary access requests and enables automatic revocation, reducing access sprawl.
How It Works
1. The project leader requests access to resources on behalf of the group, including an expiration date by default.
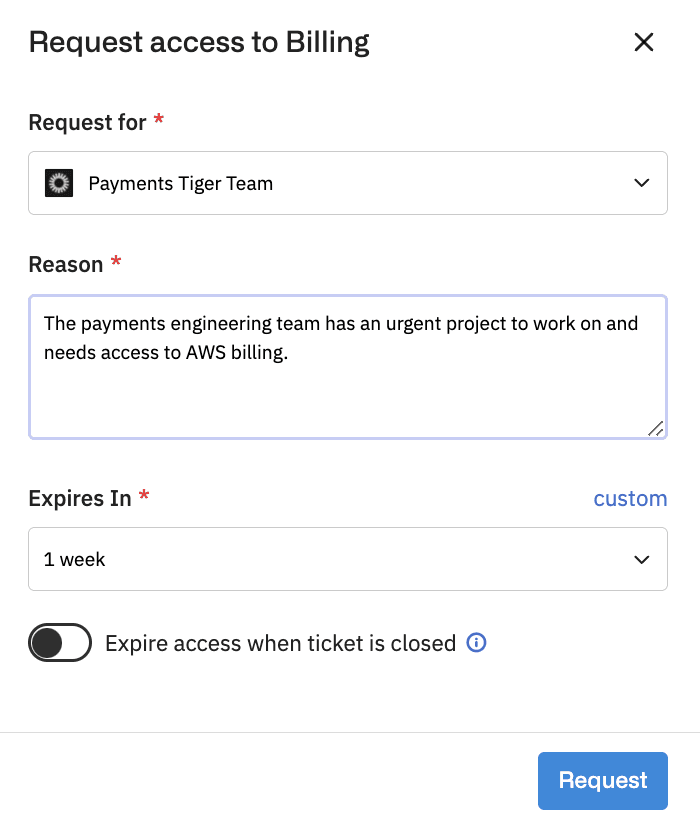
2. Approvers are notified of the request and can approve or deny it for the entire group.
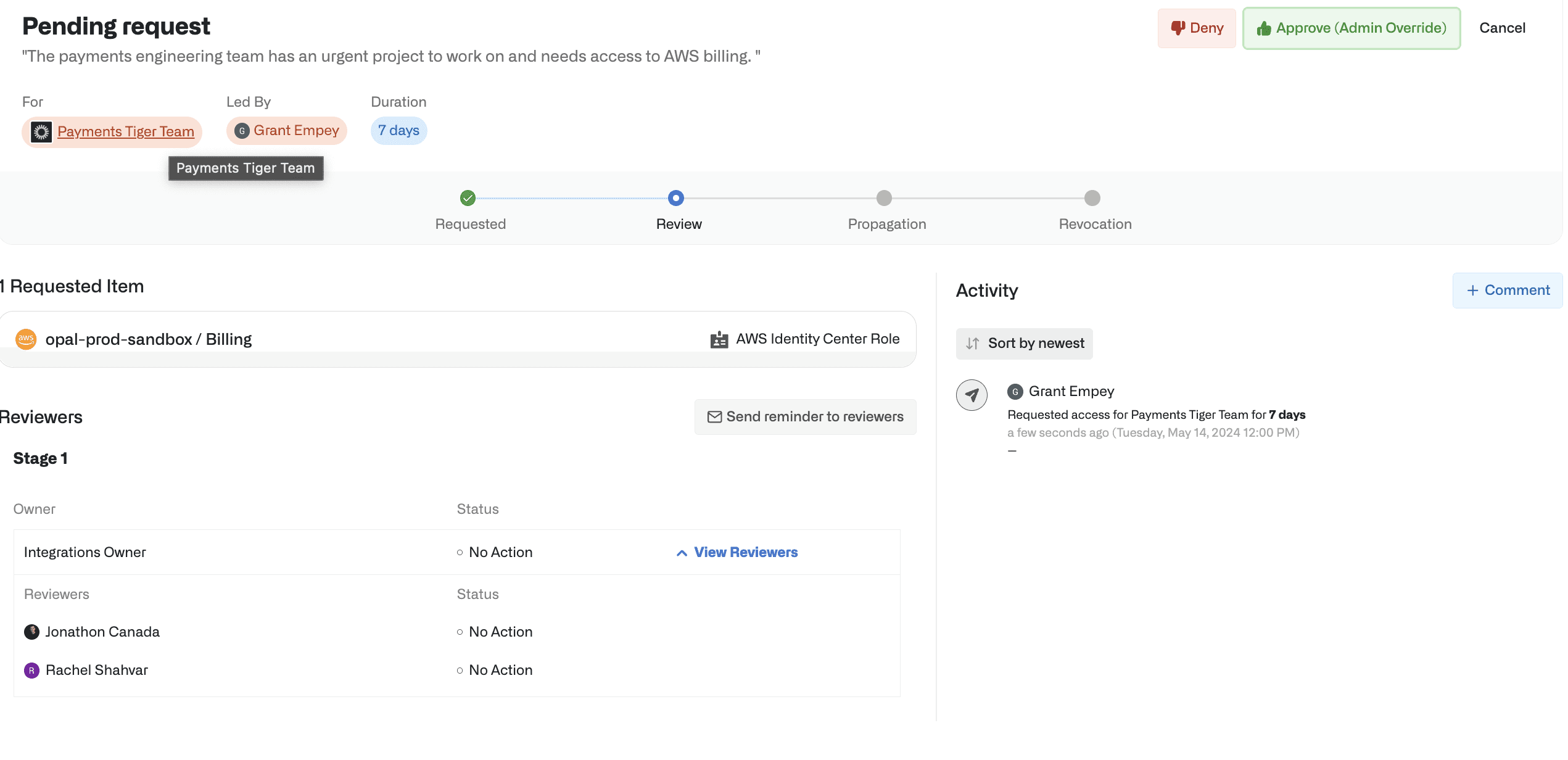
3. Once approved, the resources are added to the group, visible to the team leader for easy tracking.
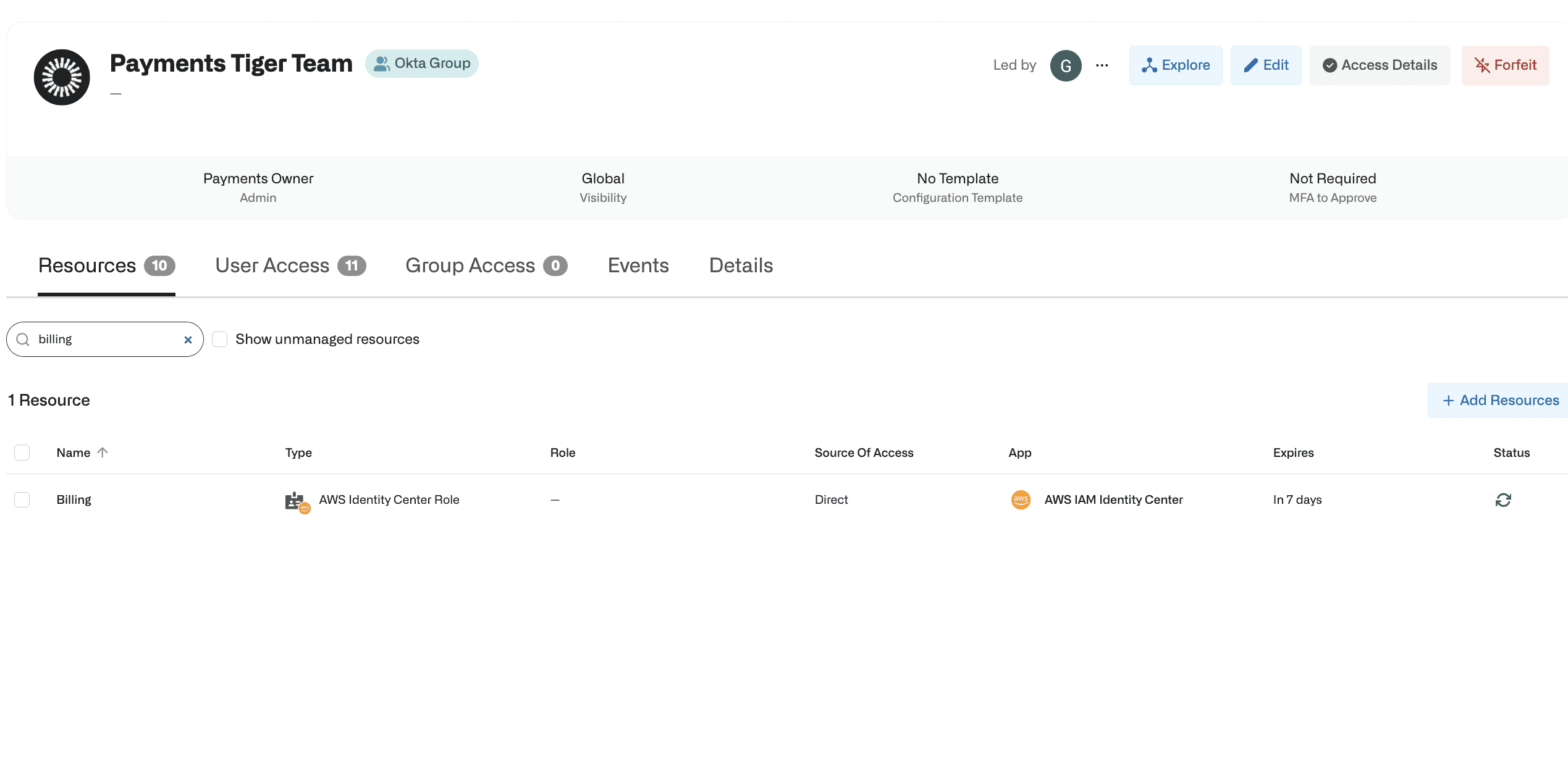
Groups can include both individual members and other groups, facilitating the addition and revocation of access for pre-existing groups.
How to Use Group Projects
The Group Projects feature is available in beta for all Opal Security customers. Interested customers can contact their Technical Account Manager to enable this feature.
What Else is New?
UAR Workflow Improvements: Teams can now implement all required access changes simultaneously after the review process, instead of individually.
Slack Workflow Enhancements: Reduced the number of clicks for MFA approvers by half.
About Opal Security
Opal Security is redefining identity security for modern enterprises. The unified platform aggregates identity and access data to provide customers with visibility and rapid control to protect mission-critical systems while accommodating the complexity and agility businesses require for growth. IT and security teams can discover anomalous identity risks and remediate them in minutes. Many global leaders, including Databricks, Figma and Scale AI, trust Opal Security to enable them to govern and adapt sensitive access quickly and securely.


