Jun 13, 2024
•
Product
Introducing Opal ↔︎ Snowflake Integration: Managing Granular Access to Critical Data
The Challenge
As enterprises expand their data footprint in the cloud, securing access to sensitive, business-critical information in processing, warehousing, and analytics platforms like Snowflake becomes more important than ever. Snowflake’s powerful and flexible Access Controls Framework allows administrators to set granular permission scopes with a high degree of customizability. However, at scale, this also means administrators must be equipped to manage complex access patterns that come with elaborate organizational policies. To enforce least privilege access to these systems and maintain regulatory compliance, Security, Infrastructure, and IT teams are often tasked to understand: who has access to a Snowflake Database? Which users have implicit access to a Snowflake Role? Which users have access to what Databases, Schemas, and Tables, and how long have they had access for? These teams not only have to be able to quickly gain context and certify access, but they also have to be able to proactively rightsize permissions and delegate approval flows while adapting to business needs and employee lifecycle changes.
The Opal ↔︎ Snowflake Integration
Opal built this integration to help customers answer key access questions and implement least privilege in their Snowflake environments. With this integration, teams can:
Quickly set up and connect Opal ↔︎ Snowflake
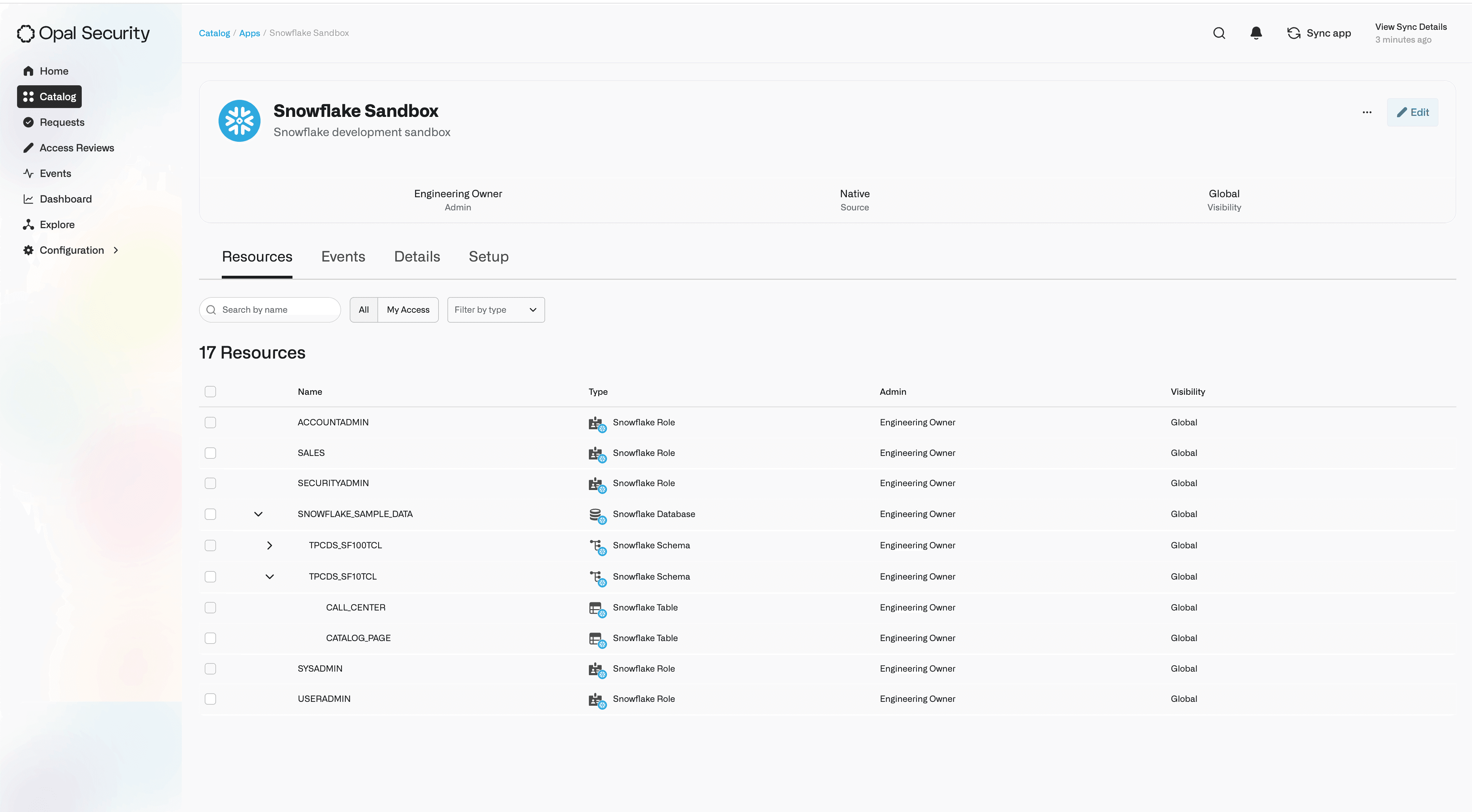
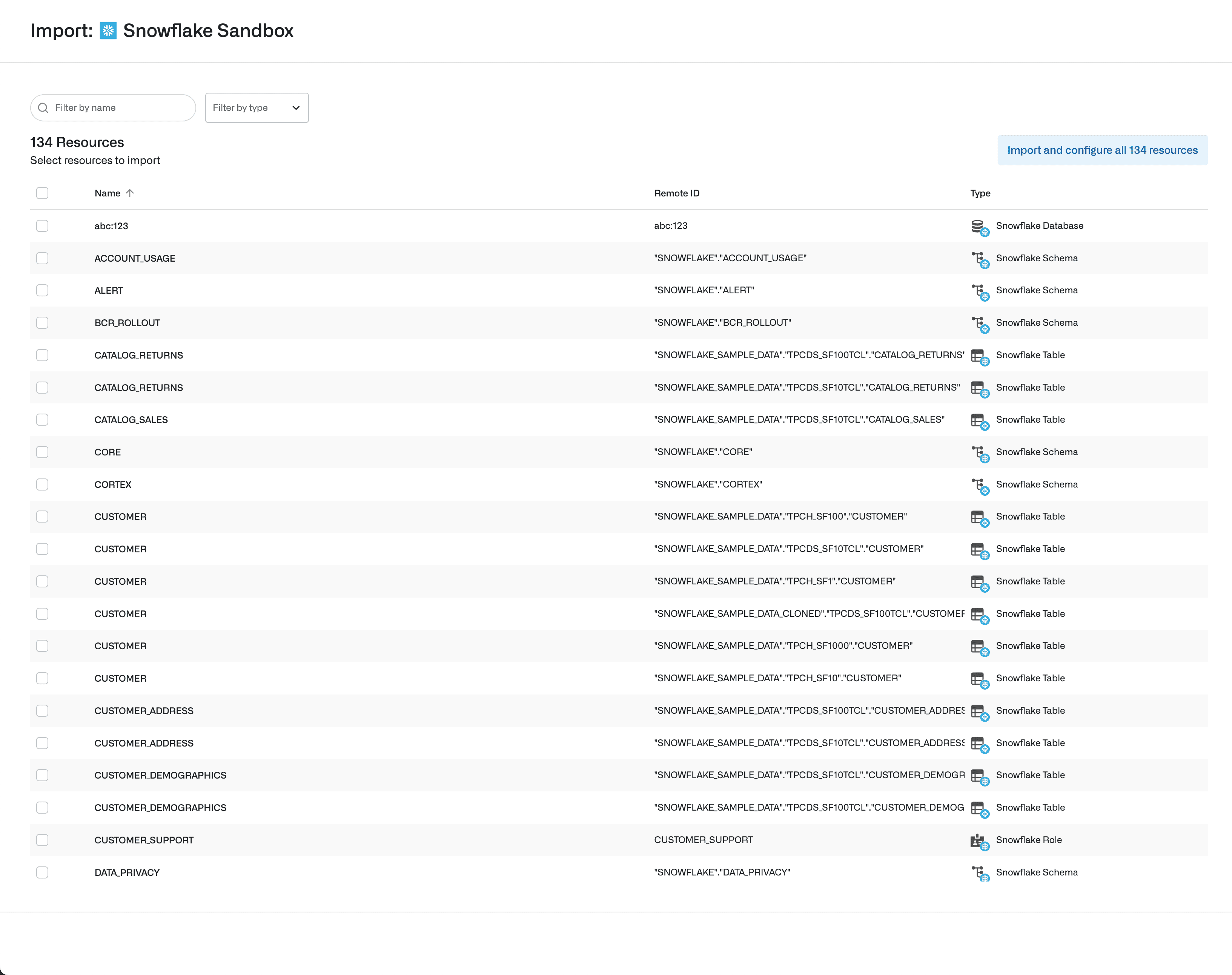
Import and sync Snowflake Roles and Securable Objects into Opal
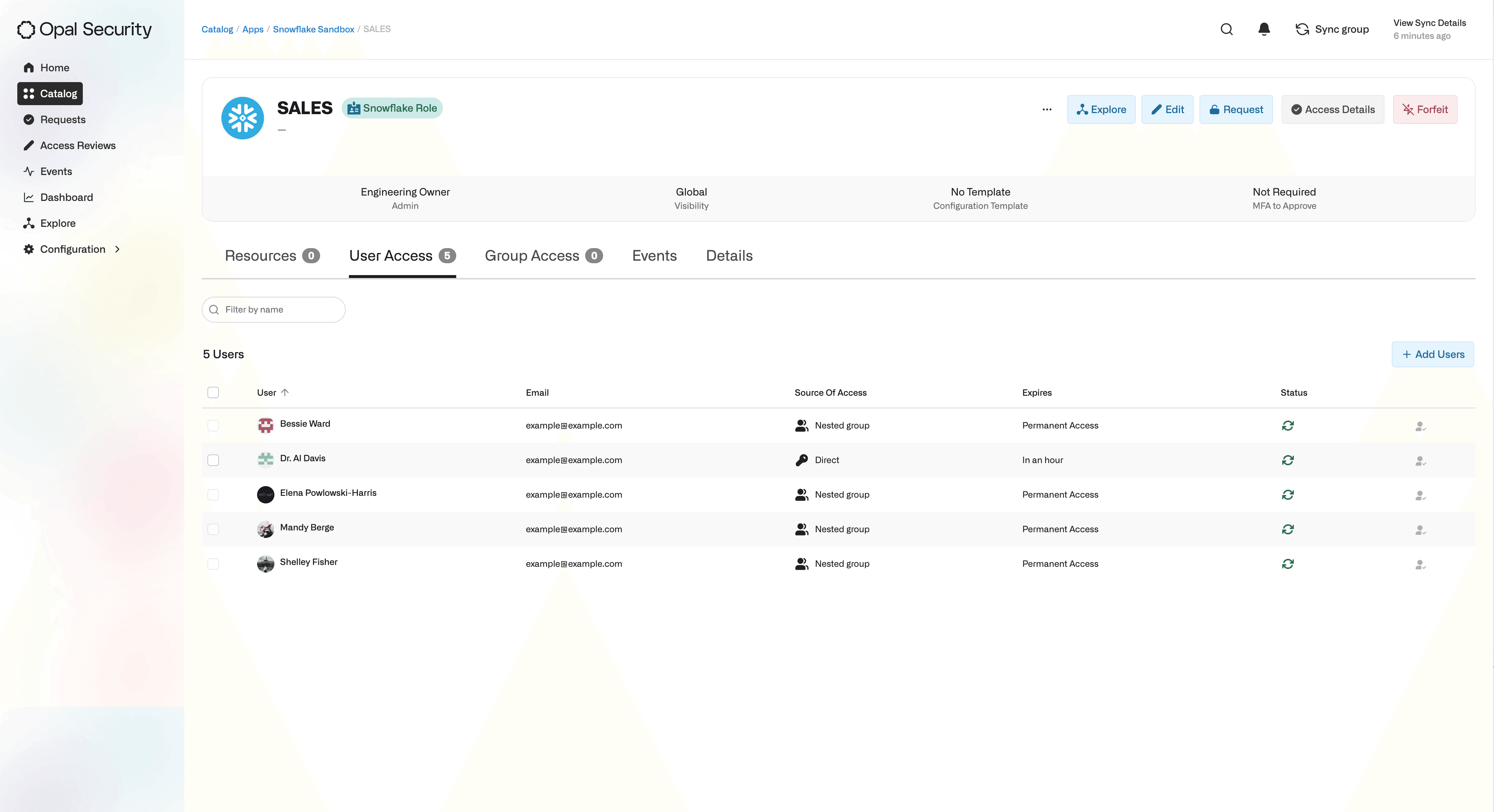
Manage which users have access to a Snowflake Role (direct & indirect)
View which Securable Objects (e.g. Snowflake Databases, Schemas, Tables) a Role has access to
Manage which users have access to Securable Objects
View granular privileges granted to each user and Role
Perform a User Access Review (UAR) on users with direct access to a Snowflake Role
Empower end users throughout the company to request JIT access to a Snowflake Role
Delegate access review and approval decisions to appropriate teams that have context around the data
Key Benefits
Simplify access: At a glance, administrators can understand which users have access to Snowflake Roles and Securable Objects and assess their security posture.
Reduce Risk: Quickly remediate on roles that are overprovisioned. For resources that contain PII or extra sensitive data, customers can easily remove users who do not require access or convert long standing to JIT access.
Enable self-service: Employees across the organization can self-service and request time-bound access to Snowflake Roles that grant them the appropriate access to datasets they need for their job. Administrators can customize request configurations and approval workflows to ensure only the necessary access gets granted.
How It Works
Importing a Securable Object like a Table will automatically create a resource hierarchy, making it easy to visualize the parent Schema and Database in Opal. Admins can choose to import only a select Snowflake Role, or automatically import it along with all the Securable Objects it has access to.
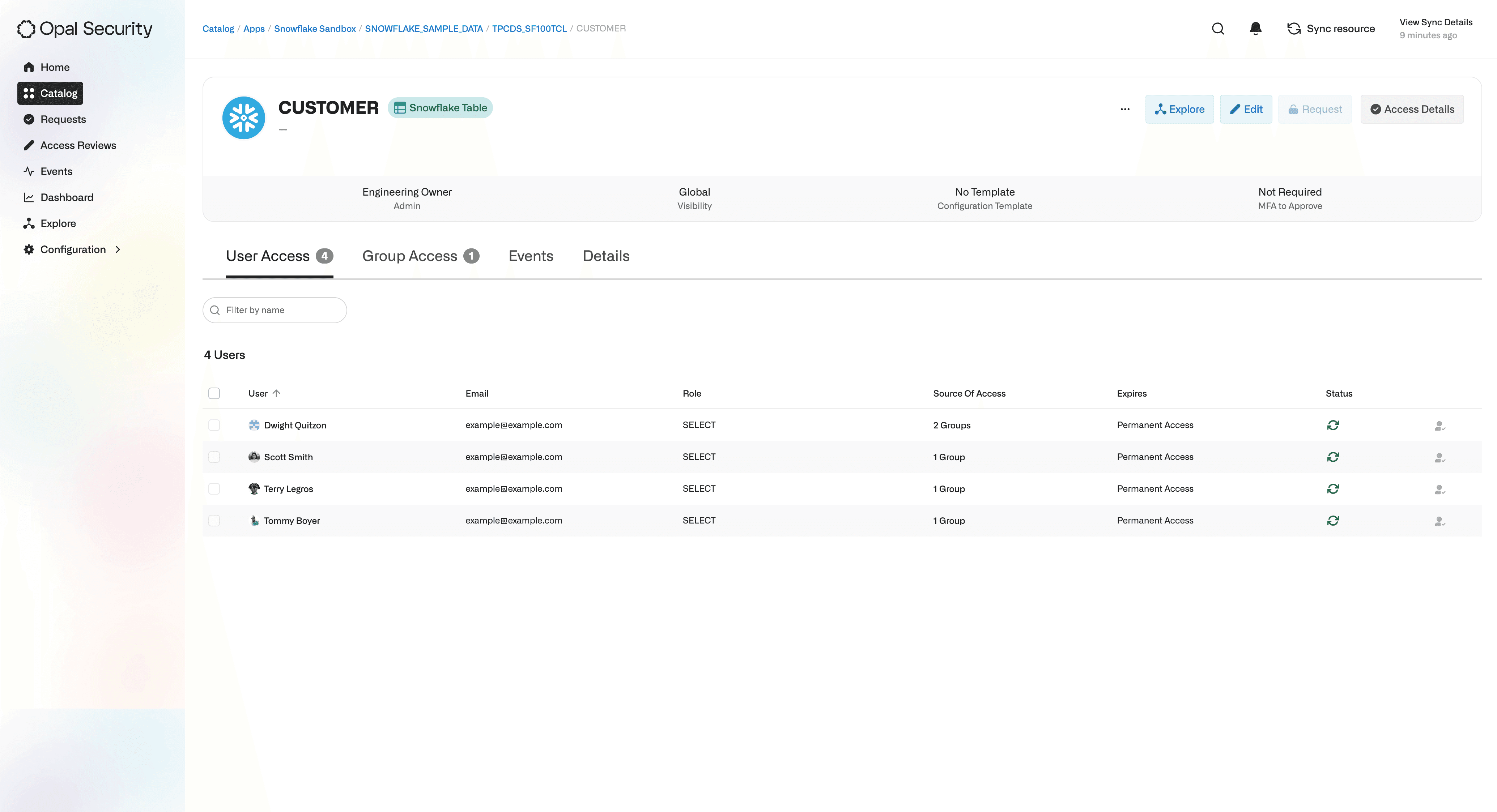
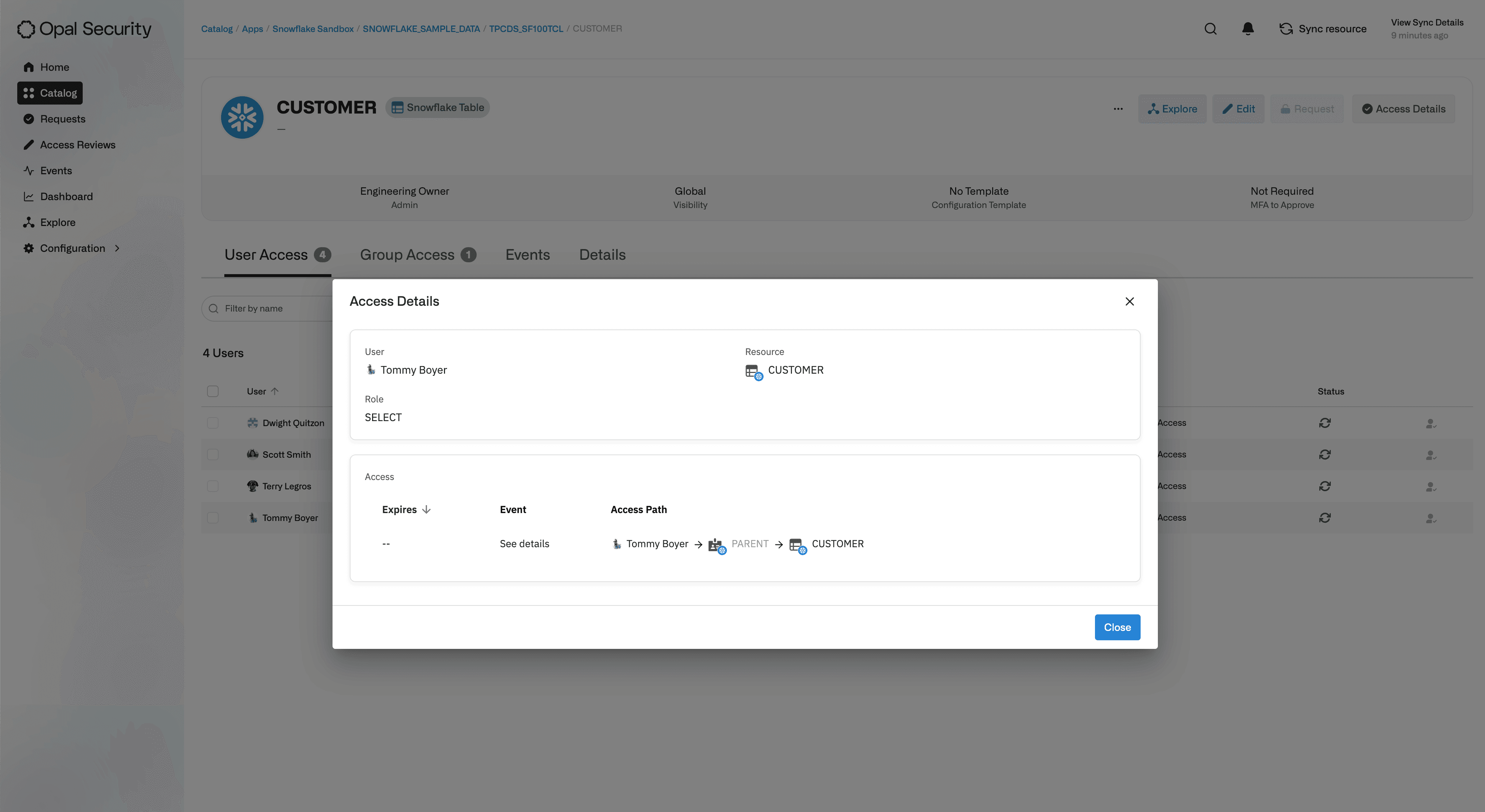
Admins can view the Privileges a user has to a Securable Object, how the access was obtained, and length of access. In this example, they can see that four users have access to the
CustomerSnowflake Table, and specifically, that Tommy Boyer has the ability to executeSELECTqueries on the table by virtue of having access to theParentSnowflake Role.
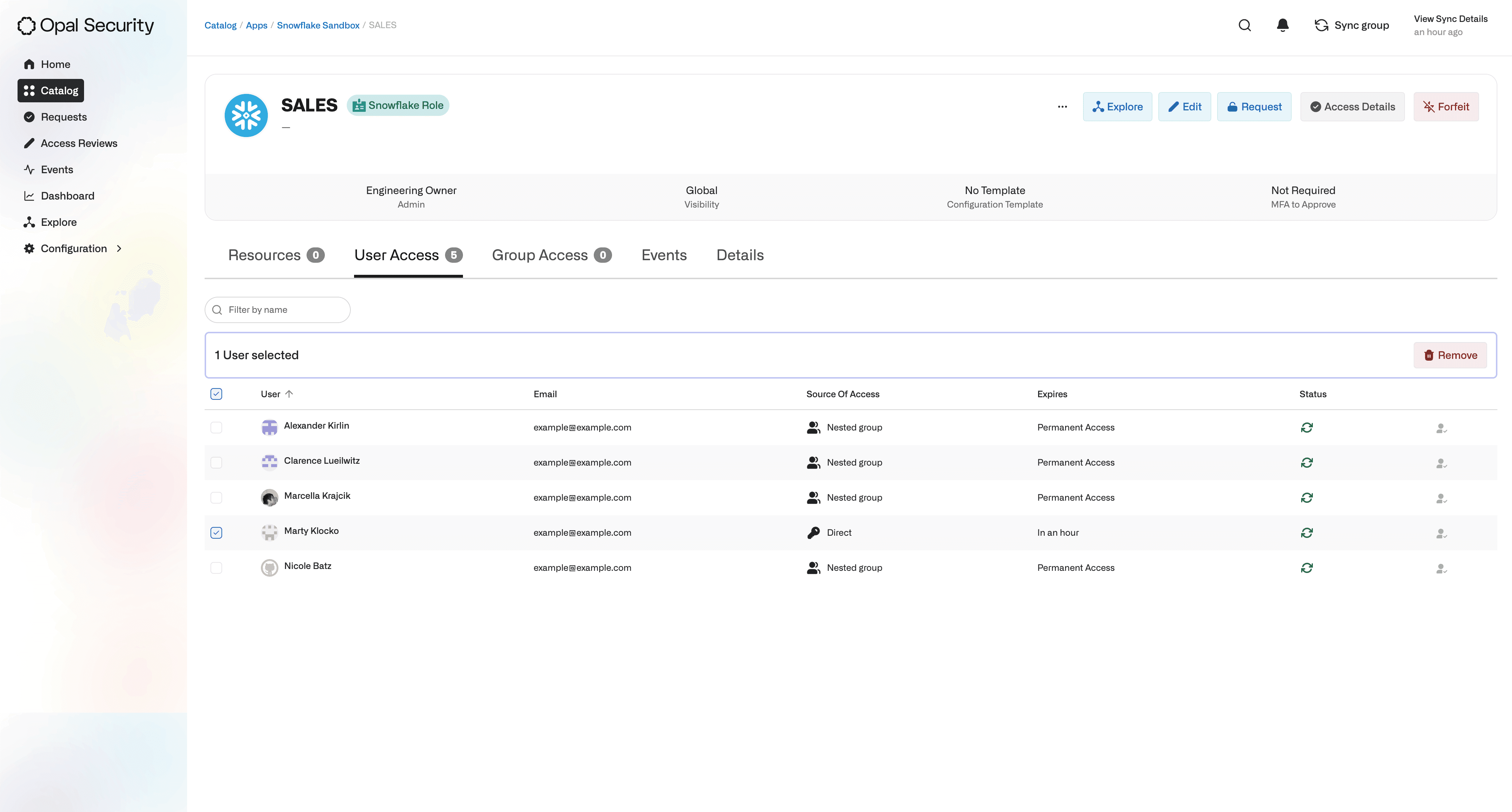
Admins can remove users with direct access to a Snowflake Role. As an example, an Opal Admin may notice that Marty Klocko, an Engineer, should not have access to the
SalesSnowflake Role. The admin can quickly remove Marty’s access or separately navigate to the Events section to understand how and why Marty was granted access to the role.
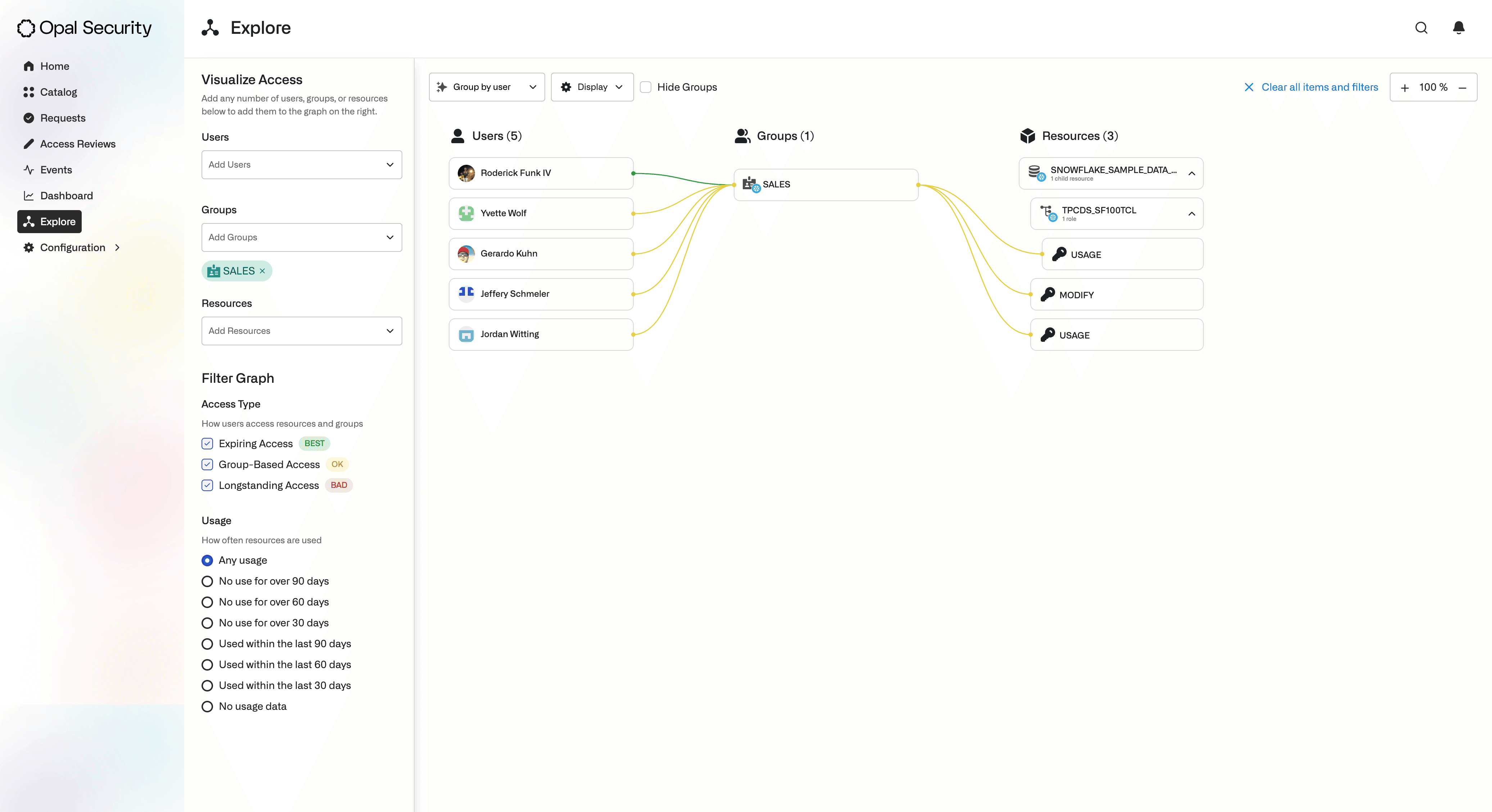
Admins can use the Explore view to easily visualize access relationships, as they can with other Opal integrations. By simply selecting the
SalesSnowflake Role, an admin can see both the list of users with access to the Snowflake Role, as well the Database, Schema, Table resources the Snowflake Role grants access to.
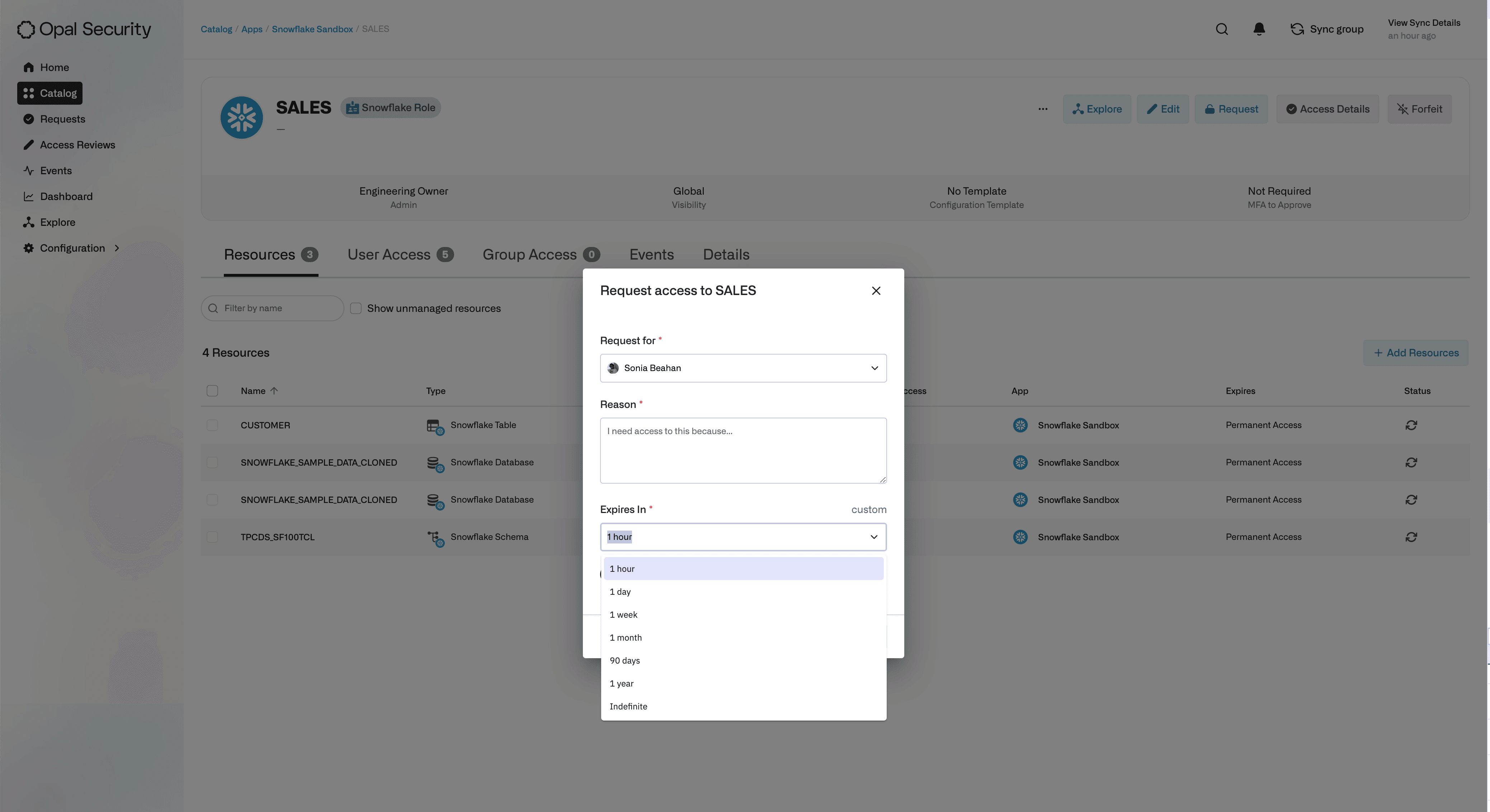
End users can request JIT access to a Snowflake Role. In this example, analyst Sonie Beahan, needs access to the
CustomerSnowflake Table to perform an investigation. Sonie can use Opal to request 1-hour access to theSalesSnowflake Role, and once their request is approved by the Sales Team Manager, Sonie will have the necessary access. After an hour, Sonie’s access will automatically expire unless extended.
How to Use the Snowflake Integration
The Opal ↔︎ Snowflake integration is available in Beta for all Opal Security customers. Interested customers can contact their Technical Account Manager to enable this feature.
About Opal Security
Opal Security is redefining identity security for modern enterprises. The unified platform aggregates identity and access data to provide customers with visibility and rapid control to protect mission-critical systems while accommodating the complexity and agility businesses require for growth. IT and security teams can discover anomalous identity risks and remediate them in minutes. Many global leaders, including Databricks, Figma and Scale AI, trust Opal Security to enable them to govern and adapt sensitive access quickly and securely.


