Jun 22, 2022
•
Product
Releasing MFA-based Approvals
Resources aren’t treated the exact same, and shouldn’t be—some are more sensitive and rarely requested, others are accessed often and can be auto-approved.
At Opal, we focus on making it easy to set resource-specific properties.
For example, here’s what it looks like under the hood of each resource, with the ability to set things like required reviewers or maximum duration of request.
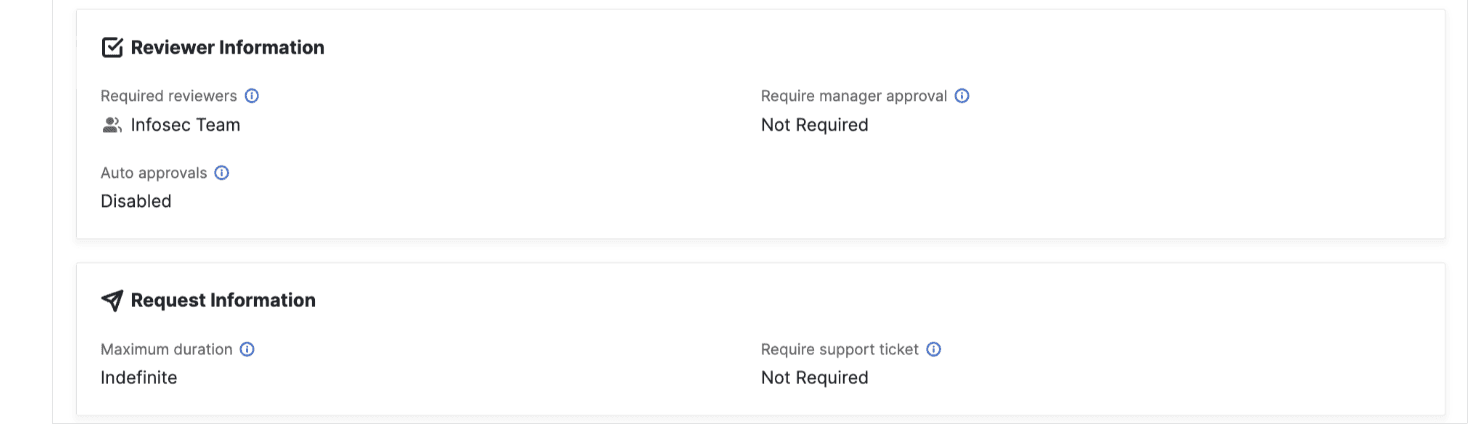
MFA Requirement for Approvers
A property we’ve added on resources is the ability to designate MFA requirements.
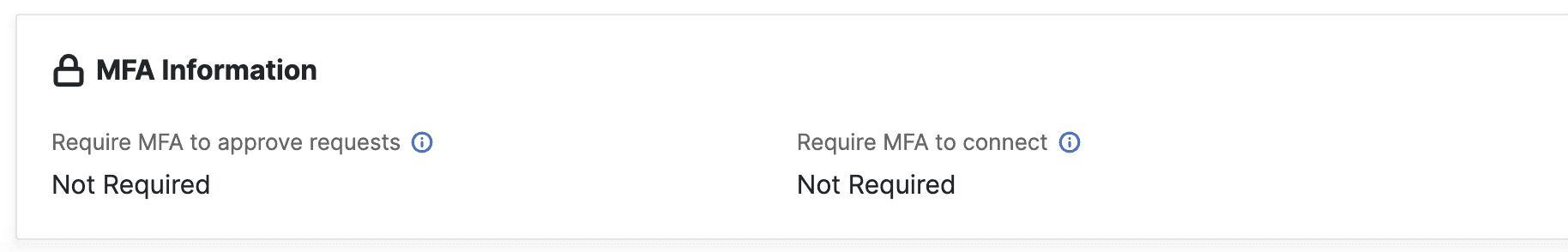
If MFA is set to Required, a reviewer will have to authenticate via MFA before being able to approve any requests. This provides an extra layer of security to resources that are particularly sensitive.

Users can also set this property on a group level, so every resource in the group requires MFA before approval.
MFA Requirement to Connect
In the same way, you can also require MFA before connecting to resources. Opal supports access to sessions for engineering infrastructure, such as EC2 servers, RDS databases, or IAM roles.
Opal supports MFA for users wanting to either connect or generate short-lived credentials.
With resource-specific properties, it’s easy to create the access workflows that match your use case.
Want to see it yourself? Contact hello@opal.dev or book a meeting for a personalized demo.
