Oct 4, 2022
•
Company
Opal Achieves SOC 2 Type 2 Compliance
Opal is proud to announce that we’ve received a clean SOC 2 Type 2 attestation report. This rigorous, independent assessment of our internal security controls serves as validation of our dedication and adherence to the highest standards for security. Opal views security as the foundation upon which our products are built and that trust with our customers is earned and maintained
Opal uses Drata’s automated platform to continuously monitor its internal security controls against the highest possible standards. With Drata, Opal has real-time visibility across the organization to ensure the end-to-end security and compliance posture of our systems.
Conducted by Linford & Co LLP, a nationally recognized CPA firm registered with the Public Company Accounting Oversight Board, this attestation report affirms that Opal’s information security practices, policies, procedures, and operations meet the rigorous SOC 2 Trust Service Criteria for security.
Additionally, we also use Opal to implement the access management controls needed for SOC 2 controls, such as user access reviews and least privilege controls
How does Opal use Opal to implement SOC 2 controls?
1. Implement Least Privilege
The principle of least privilege is ensuring that people users have access to only what they are strictly required to do. Not only is this a foundational security principle, but its a huge part of the SOC 2 security framework:
Least-Privileged Policy for Customer Data Access (CC2.1, CC5.2)
System Access Control Policy (CC4.1, CC6.2, CC6.3)
Only authorized Opal personnel can push or make changes to production code (CC8.1)
Appropriate levels of access to infrastructure and code review tools are granted to new employees within one week of their start date (C1.1, CC6.1, CC6.2, CC6.3, PI1.5)
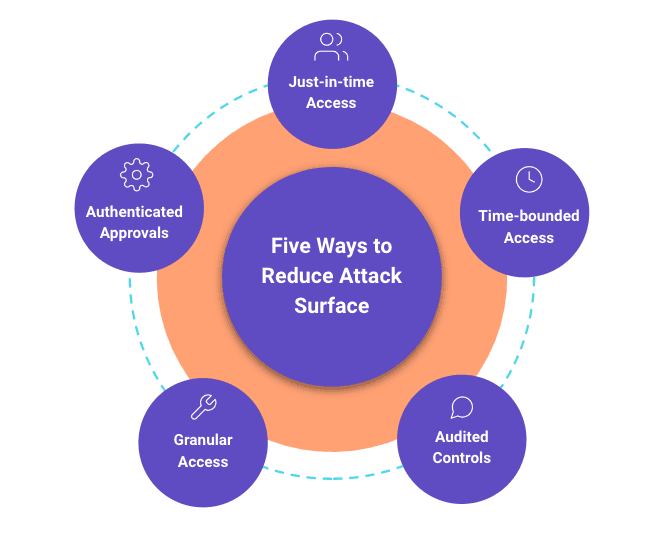
Using Opal to implement least privilege, we are able to effectively limit the blast radius of a potential security breach. At Opal, we think about the five vectors of attack surface:
Just-in-time Access: Access to sensitive infrastructure is not given by default. It must granted just-in-time and is fully audited
Time-bounded Access: Access to infrastructure, credentials, and sessions are automatically auto-expiring
Granular access: Access to production infrastructure is granular and not overly permissive
Authenticated approvals: Approvers must validate their identity using 2FA
Audited controls: All access is audited and documented
2. Automated User Access Reviews
Conducting user access reviews can be daunting, confusing, and time-consuming process. However, they are a necessary part of the SOC 2 framework:
Periodic access reviews (CC4.1, CC6.2, CC6.3)
Using Opal, we are able to automate the manual processes reduce friction and confusion through automation:
All user listings for critical applications are automatically snapshotted
Reviewers are automatically assigned from resource owners and are notified via Slack
After conducting a self-service user access review, all access changes are automatically propagated
An auditor-friendly access review summary report is automatically generated

As more enterprises look to process sensitive and confidential business data with cloud-based services like Opal, it’s critical that they do so in a way that ensures their data will remain safe. Our customers carry this responsibility on their shoulders every single day, and it’s important that the vendors they select to process their data in the cloud approach that responsibility in the same way.
We welcome all customers and prospects who are interested in discussing our commitment to security and reviewing our SOC compliance reports to contact us.
About SOC 2
SOC 2 stands for System and Organization Controls (SOC). It's an independent, third-party assessment of an organization's security practices. A SOC 2 Type I report is an attestation of controls at a service organization at a specific point in time. A SOC 2 Type II report is an attestation of controls at a service organization over a minimum six-month period
About Opal
Opal is the unified identity platform for modern enterprises. Opal aggregates identity and access data to provide visibility and defense-in-depth infrastructure for mission-critical systems. Enterprises can discover anomalous identity risks with the product and remediate them in minutes. The world's best companies trust Opal to govern and adapt sensitive access.
Want to see it yourself? Contact sales@opal.dev or book a meeting here for a personalized demo.
About Drata:
Drata is the world's most advanced security and compliance automation platform with the mission to help businesses earn and keep the trust of their users, customers, partners, and prospects. With Drata, companies streamline framework compliance like SOC 2, ISO 27001, HIPAA, and many more through continuous, automated control monitoring and evidence collection, resulting in a strong security posture, lower costs, and less time spent preparing for annual audits. The company is backed by ICONIQ Growth, Alkeon Capital, Salesforce Ventures, GGV Capital, Cowboy Ventures, Leaders Fund, Okta Ventures, SVCI, SV Angel, and many key industry leaders. For more information, visit drata.com.
