Sep 27, 2022
•
Resources
Opal and Okta - Better Together
Summary
Opal and Okta work better together to deliver a comprehensive identity and access management solution. Opal integrates with Okta for central integration, but extends its functionality with workflow orchestration. In a future blog post, Opal will deep dive into the actionable insights use case.
The Identity and Access Management Journey
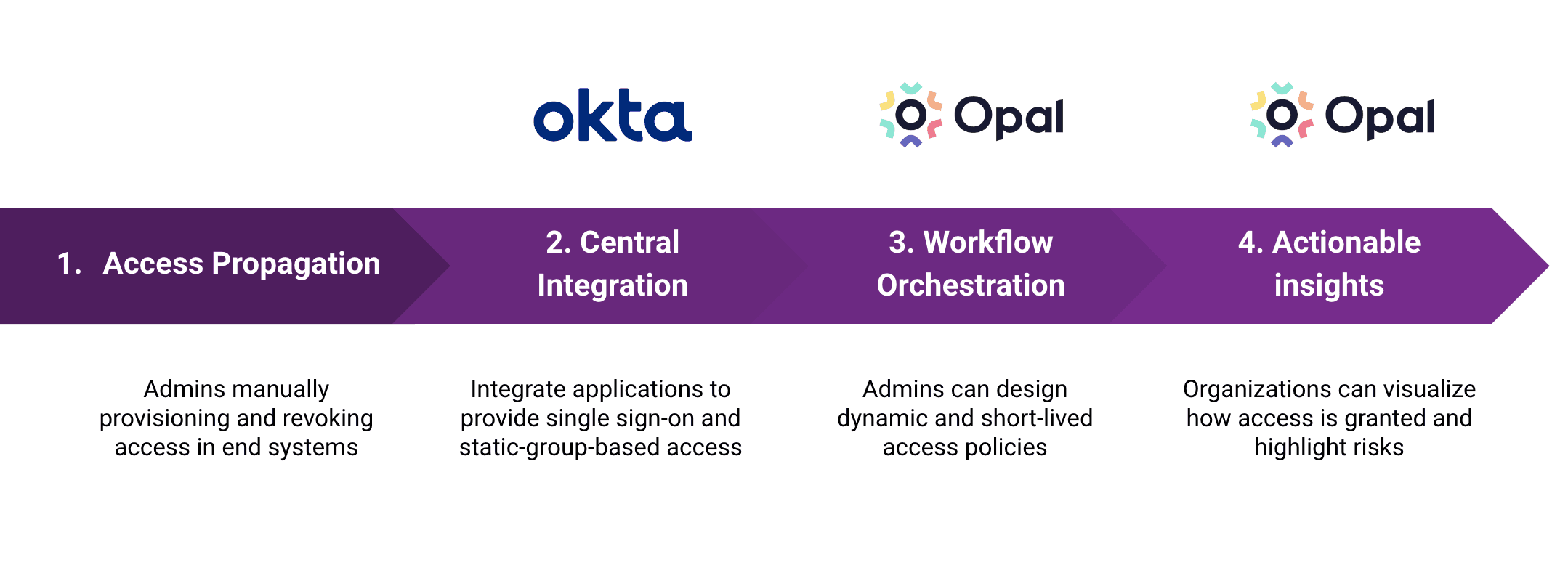
At Opal, we focus on working with security leaders, from high growth startups to the Fortune 500. As the bedrock of most security programs, identity and access management (IAM) is a journey and can be broken down into major maturity phases:
Manual access propagation: This phase involves admins manually provisioning and revoking access in end systems. Often times, access ledgers are maintained manually in spreadsheets.
Central integration: Many companies will implement an identity provider, such as Okta, to be the central integration layer to provide single sign-on (SSO) and static group-based access
Workflow orchestration: Access management solutions enable admins to design dynamic and short-lived access policies and orchestrate processes such as identity governance, privileged access management, and user access reviews.
Actionable insights: In the final phase, organizations are able to clearly visualize how access is granted and highlight risks based on static and dynamic inputs
Our customers have been using Opal and Okta together to implement a holistic IAM strategy in their security journey. With over 7,000 integrations, Okta is the leading provider for how users authenticate into applications using SSO and MFA. By integrating with Okta, Opal imports users, groups, and Okta applications. Opal supercharges the integration experience with its own connectors in order to integrate with granular application resources and access levels for complex systems such as AWS, GCP, Salesforce, and more. Resources are the individual components within applications such as RDS databases for the AWS application. Access levels are the specific permissions such as Read Only for the Github application. Overall, Opal and Okta provide employees with catalog of granular permissions and admins can configure context-based access policies.
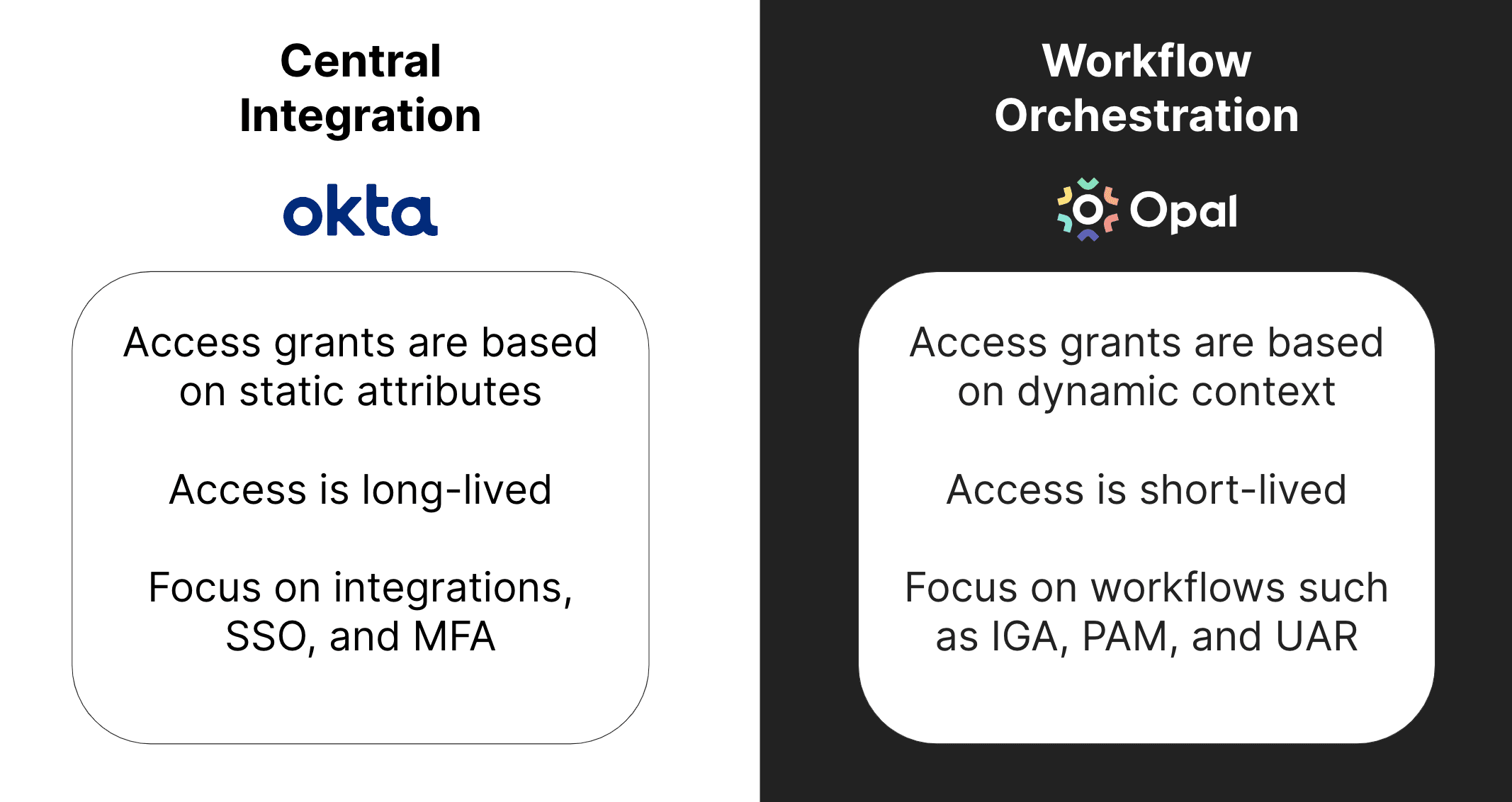
Central Integration vs. Workflow orchestration
Identity providers, such as Okta, connect with applications and Human Resources Information Systems (HRIS). Okta grants access to a core set of applications based on organizational information, such as department, team, and cost center. This is known as birthright access.
While this is useful to ensure that employees have day-one access, this type of access is static. With identity providers, removing access is often manual and rarely performed. At many companies, employee access only accumulates over time - increasing the risk for insider threats. In 2021, 51% of Twitter employees had privileged access to production systems and data. The fast changing nature of enterprises means that mapping access based on static attributes isn’t sufficient for complex needs.
Instead, companies need to compliment central integration with workflow orchestration to grant dynamic and just-in-time access - in other words access that is granted and revoked on an as-needed basis.
Opal + Okta: Better Together
Using Okta and Opal, companies can tackle complicated process challenges:
1. Empower employees with self-service
In order to orchestrate access, companies need varying granularity from applications to permissions. With Opal and Okta, employees can browse Okta apps, Okta groups, but also native permissions using Opal’s connectors, such as Read Only RDS database from AWS or Sales Engineering Role in Salesforce. Ultimately, this offers transparency, flexibility, and security as employees can request specifically for what they need - nothing more and nothing less.

2. Protect organizations with context-based access
Rather than granting static access all of the time, Opal limits the amount of access given by leveraging context-based access. The most obvious form of context is through access requests. Opal makes just-in-time access frictionless. Approvals are delegated to system owners and admins with the most context. Provisioning is automated with Slack.
Opal can also automate regular occurrences of context-based access. One of the most common workflows is to automate on-call access. Rather than granting longstanding privileged access to a large group of engineers or manually revoking access with calendar reminders, Opal can integrated with on-call providers like PagerDuty and OpsGenie. With this integration, you can automatically grant privileged access to engineers who are on-call and revoke access when they are off-call!

3. Utilize developer-centric workflows
Once granular AWS permissions are bound to Okta groups, Opal extends its native integrations to unlock powerful privileged access management workflows.
Identity-based access: Unlike traditional PAMs that require you to check-in / check-out shared credentials, Opal federates access to RDS databases, EKS clusters, and EC2 servers directly using an one-to-one mapping for identity
Auto-expiring credentials: Manual credential rotation is both an operational burden and security risk. With Opal, developers can easily generate identity-based credentials that automatically expire after 15 minutes.
CLI access: Meeting engineering teams in their processes today, developers can use Opal’s CLI to start IAM roles, database sessions, Kubernetes roles, SSH sessions and more!
Dynamic IAM role creation: In addition to requesting for specific roles, Opal can be used to dynamically generate new IAM roles.

4. Apply governance policies to Okta groups
Leveraging the power of self-service and delegated management, Opal enables organizations to set up powerful governance policies. For Okta groups and apps, Opal allows admins to configure guardrails such as:
Visibility: Configure which resources and groups users can see
Required reviewers: Set up multi-stage approvals with managers and/or system owners
Custom fields: Ensure consistency by creating custom fields that requestors have to fill out
2FA: Protect critical resources by requiring MFA to approve requests
Max duration: Enforce short-lived access by setting max request durations
Best of all, enterprises can configure policies at scale using Opal's APIs.

5. Conduct user access reviews across the organization
Designed from the ground up for compliance teams, Opal enables organizations to kick off self-service access reviews with a compliance dashboard. Reviewers are dynamically assigned based on admin or manager and are notified via Slack. Once they are in the platform, reviewers have a guided journey to change accept or modify access. All changes are automatically propagated via Opal and are captured in an auditor-friendly report.

About Opal
Opal is the unified identity platform for modern enterprises. Opal aggregates identity and access data to provide visibility and defense-in-depth infrastructure for mission-critical systems. Enterprises can discover anomalous identity risks with the product and remediate them in minutes. The world's best companies trust Opal to govern and adapt sensitive access.
Want to see it yourself? Contact sales@opal.dev or book a meeting here for a personalized demo.
