May 8, 2024
•
Product
Scaling and Automating Identity Security with Opal and Tines
As enterprises grow and modernize their technology stacks, protecting unauthorized access to critical applications and data across the cloud and on-prem becomes more important than ever. Major cloud providers like AWS, GCP, Azure and SaaS tools like Github, Salesforce, Slack are all sources containing rich troves of sensitive data. A company’s ability to appropriately grant and revoke fine-grained access to such systems for an ever-evolving workforce directly impacts its ability to maintain a strong Identity Security posture. While Security, IT, and Infrastructure teams do their best to define and implement least privilege, managing this at scale is almost impossible due to the speed and complexity of businesses today.
To tackle this, Opal and Tines are partnering to help teams protect and manage access to their critical resources in an automated fashion.
With Opal’s data-centric identity platform that integrates seamlessly into an organization’s application ecosystem, teams can easily gain visibility on who has access to what, feel empowered to delegate access policies, and swiftly remediate overprovisioned access .
With Tines’ intuitive and powerful automation platform and extensive repertoire of event-based templates, teams can swiftly operationalize the repeatable, high-overhead tasks that often cause burnout or friction between organizations.
Used in combination, Opal and Tines can help provide direct access management and remediation capabilities easily, effectively, and efficiently.
Sample Opal x Tines Use Cases
To get started, we’ve put together a few common use cases we’ve seen customers employ:
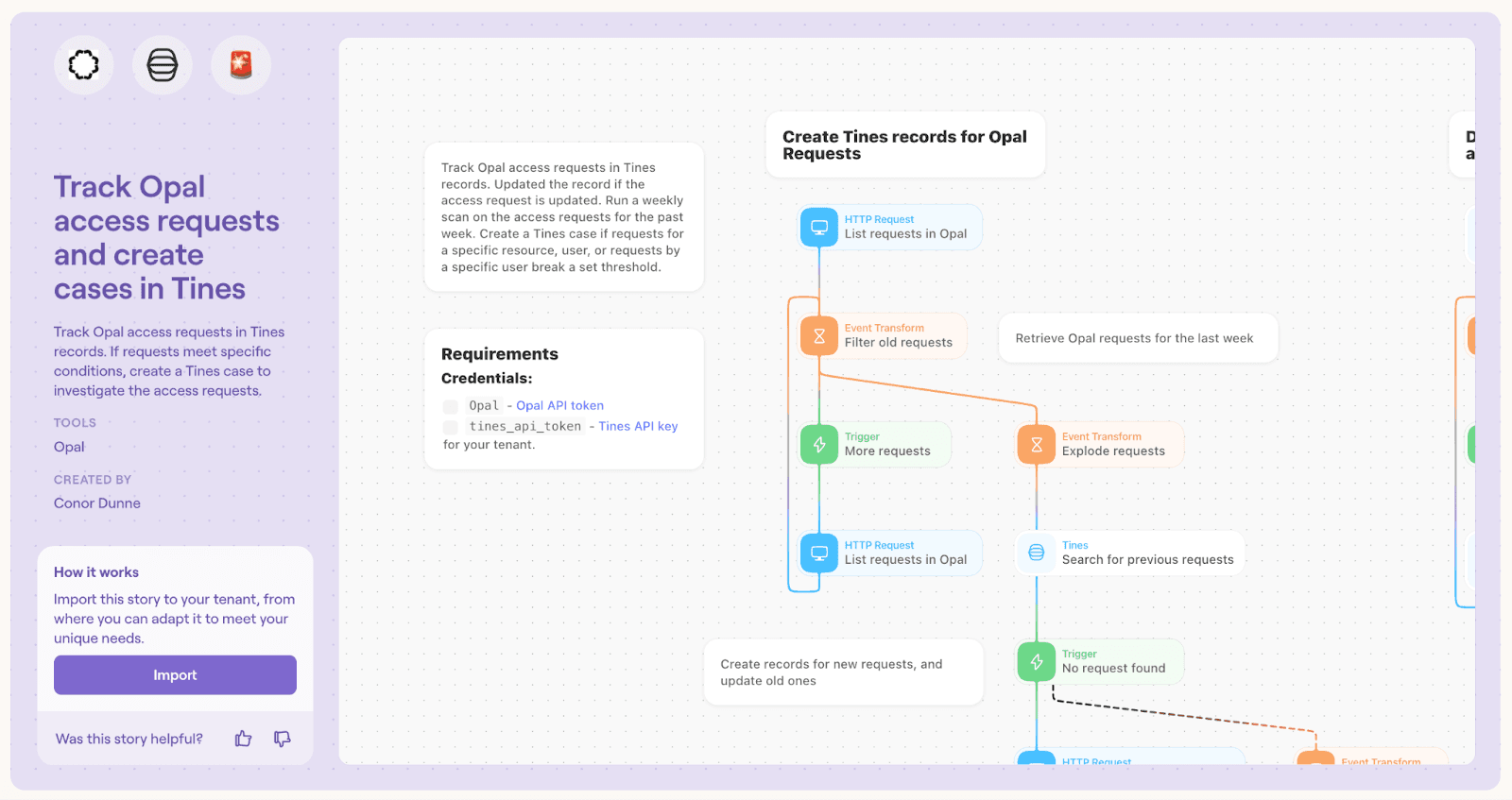
Use case 1: Alerting on anomalous access behavior
In this use case, customers can track access requests in Opal, and if the content of the requests meet specific conditions, Tines creates a Tines case to investigate the access requests.
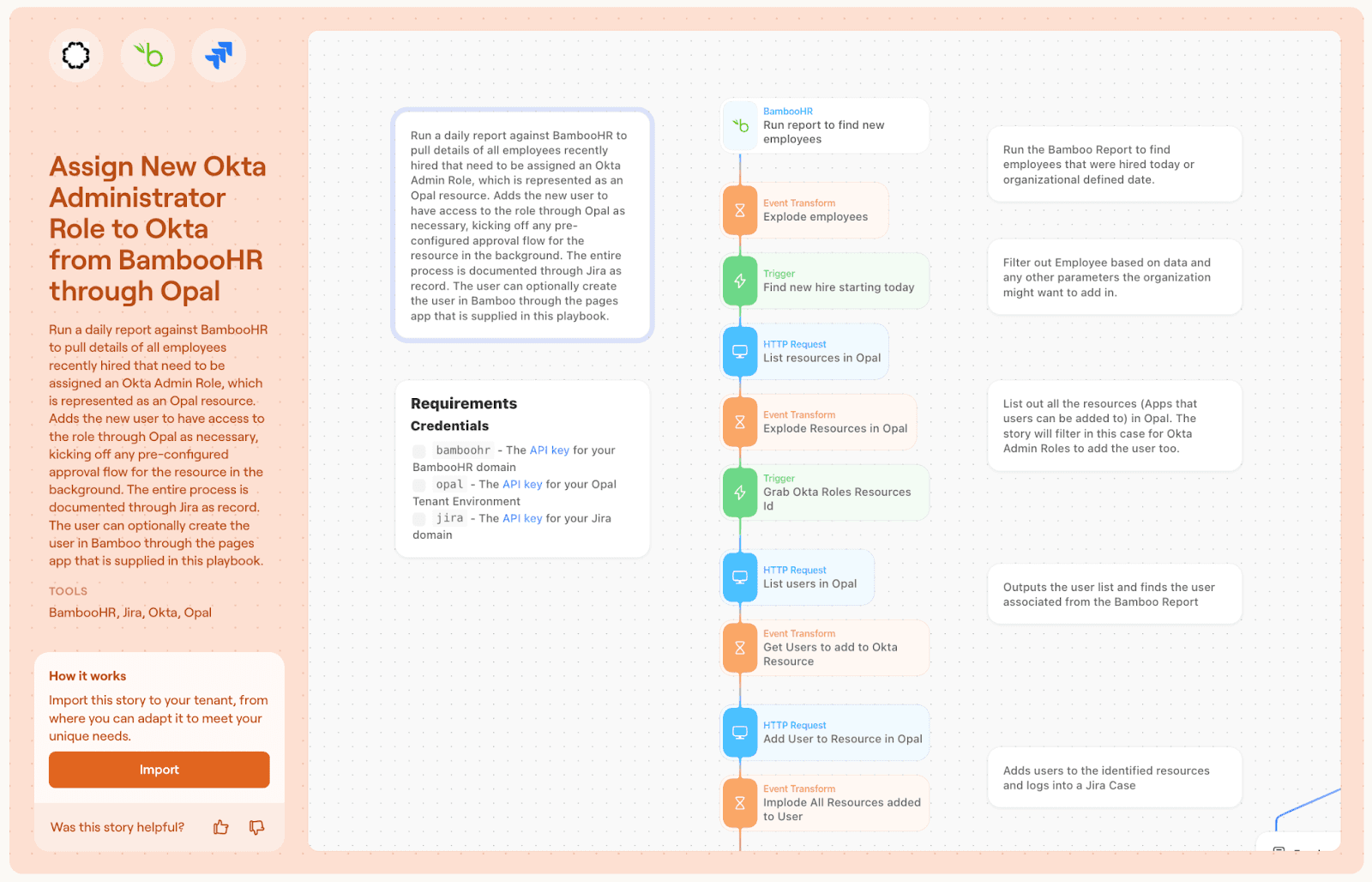
Use case 2: Adding a new team member automatically to a group or resource and tracking the change in a ticketing system
In this use case, customers can create a Tines trigger against a “New Hire” event from their HRIS of choice, automatically add the user to the desired Opal-managed group or resource, and generate a Jira ticket to record the change.
At Opal, we’re dedicated to ensuring that our customers have the tools they need to securely manage access to their applications and data from day one, and we look forward to building and sharing more use cases with the community.
Benefits of Opal x Tines:
Scalable Implementation of Least Privilege: Opal provides holistic visibility, actionability, and control over a customer’s Identity Security posture while Tines helps connect the dots with flexible and proactive automation stories.
Seamless, low-effort integration with existing tooling and workflows: Opal and Tines work with a variety of end systems to link together events, triggers, and access data for quick remediation capabilities.
Reduced manual overhead on repetitive access tasks: The days of manually managing access against a sprawling set of resources and manually creating change management tickets are limited with this powerful combination of access data and automation.
Learn More
Try Opal and Tines out today to start securing your identity perimeter at scale. If you would like to learn more about how Opal can help your team in this journey, don’t be shy and reach out to us at: hello@opal.dev.

