Aug 14, 2024
•
Product
Introducing GCP Service Accounts: Managing NHI Access in Google Cloud
The Challenge
Roughly 94% of organizations do not have full visibility into their non-human identities, making these highly vulnerable and often privileged identities a prime target for attackers. In GCP, machine identities such as Service Accounts represent applications or workloads – rather than humans – and are often bound to privileged IAM Roles with access to critical data. Anyone who is able to authenticate as the Service Account therefore inherits its permissions to perform sensitive actions. Given the ubiquity of Service Accounts in GCP, securely managing them is crucial for protecting organizations against privilege escalation, spoofing, non-repudiation, and information disclosure. To maintain a least-privilege identity posture, security and infrastructure teams must be able to quickly identify, track, and manage not only who has access to Service Accounts, but also what resources those Service Accounts have access to (e.g. GCP Compute, Cloud SQL Database, Bigquery Datasets). Without an easy way to understand these User <> Service Account and Service Account <> Resource relationships, teams struggle to effectively analyze and remediate risks posed by different identity types at large.
GCP Service Accounts in Opal
In order to provide security and infrastructure teams both the visibility and control needed to reduce the risks associated with overprovisioned Service Accounts, Opal has expanded identity type coverage in our native GCP integration to include Service Accounts. Since they are by nature both resources and principals, we allow customers to manage which employees have access to Service Accounts, and we additionally allow customers to manage what resources these Service Accounts have access to. With this expansion, our users are equipped to truly implement least privilege in GCP at scale.
Key Benefits
Deeper Visibility into Attack Surface: Including Service Accounts as a first-class entity in the identity fabric alongside human users allows customers to track, inventory, and gain a comprehensive view of the attack surface in GCP environments.
Reduce Risk: The blast radius associated with unauthorized use or impersonation of privileged Service Accounts can be far reaching especially considering that each GCP Project can have up to 100 Service Accounts by default. Reducing who can utilize the Service Account, and for how long, and what the Service Account can access is key to reducing the blast radius.
Manage Least Privilege Posture: Least Privilege is about ensuring only the necessary access is granted to an entity, and only for the time required to do the job. By identifying and removing overprovisioned access to and from Service Accounts, Security teams can quickly improve the Least Privilege posture of their organization.
How It Works
Opal provides a top level view of all your non-human Identities alongside users. From there, admins can browse how many resources these identities have access to and what app they belong to.
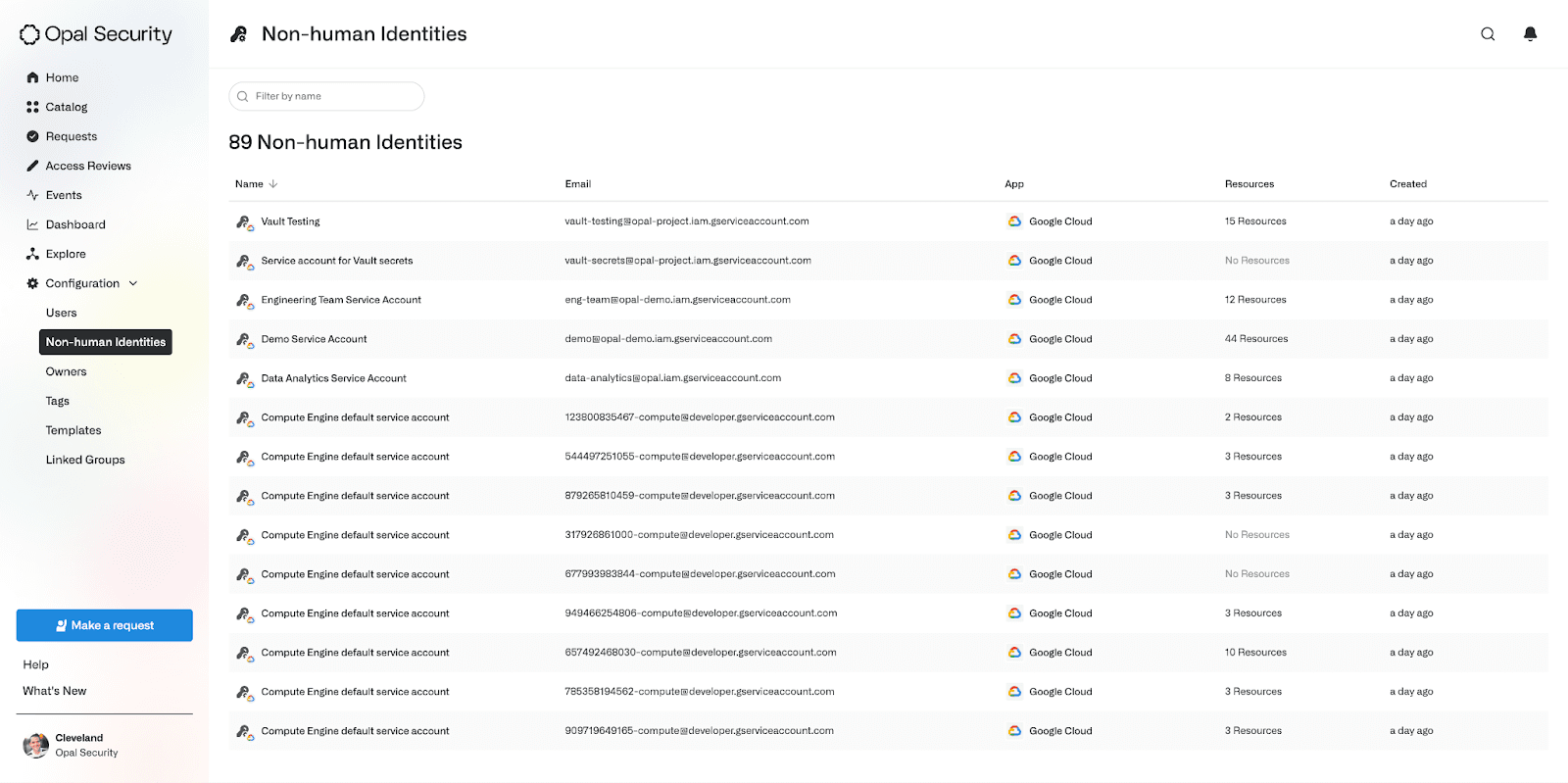
Admins can view all users that have access to a Service Account, including what role they have, when their access expires, and how they obtained the access. In the below example, Cynthia has access to the Service Account Admin role through a group which expires in a year, whereas Roberto has direct access to the Token Creator role expiring in a day. Emanuel is an Owner of the entire GCP Organization, so he inherited that role onto the Service Account as well.
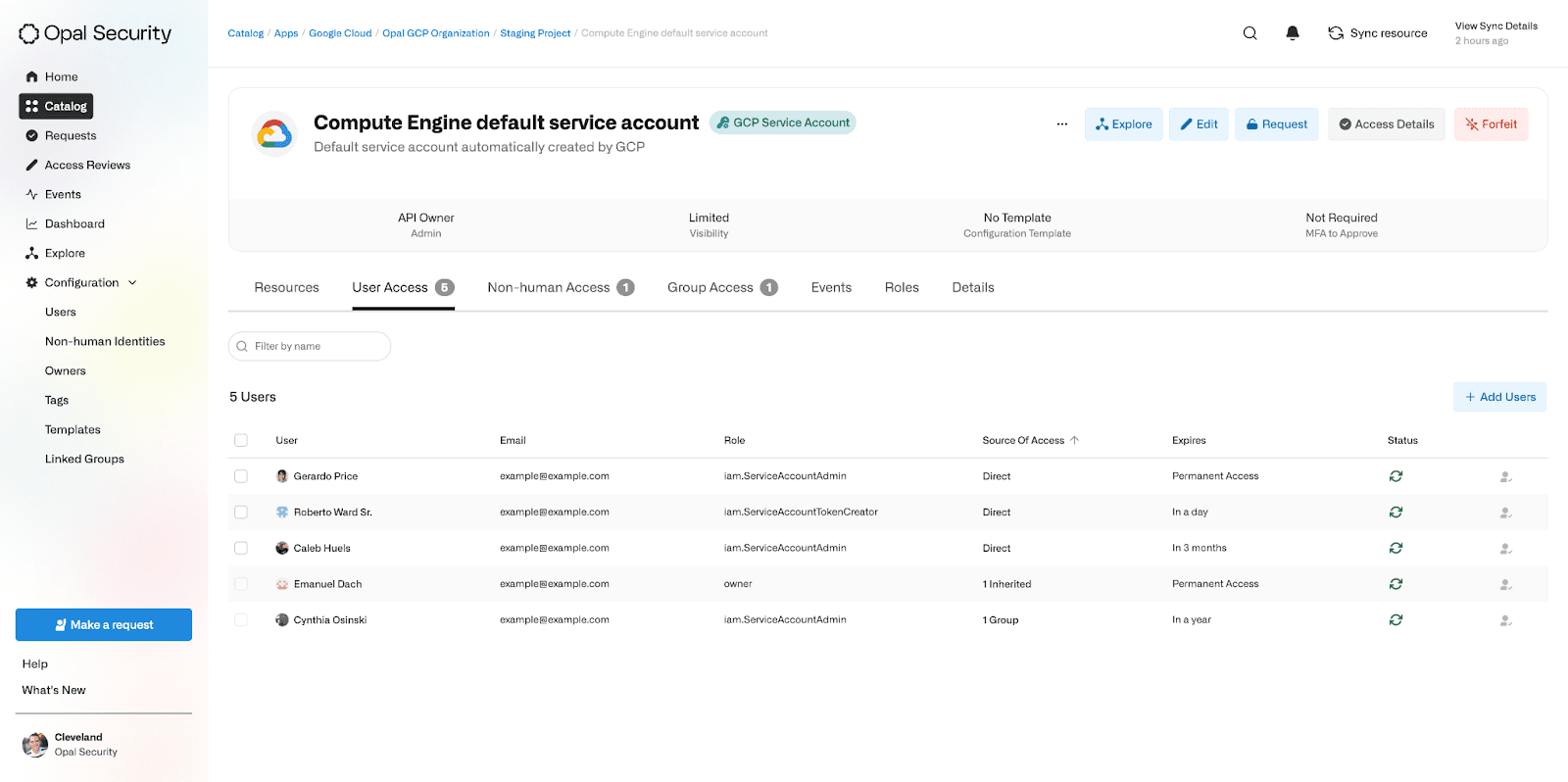
End users are able to request just-in-time (JIT) access to these Service Accounts as they need it.
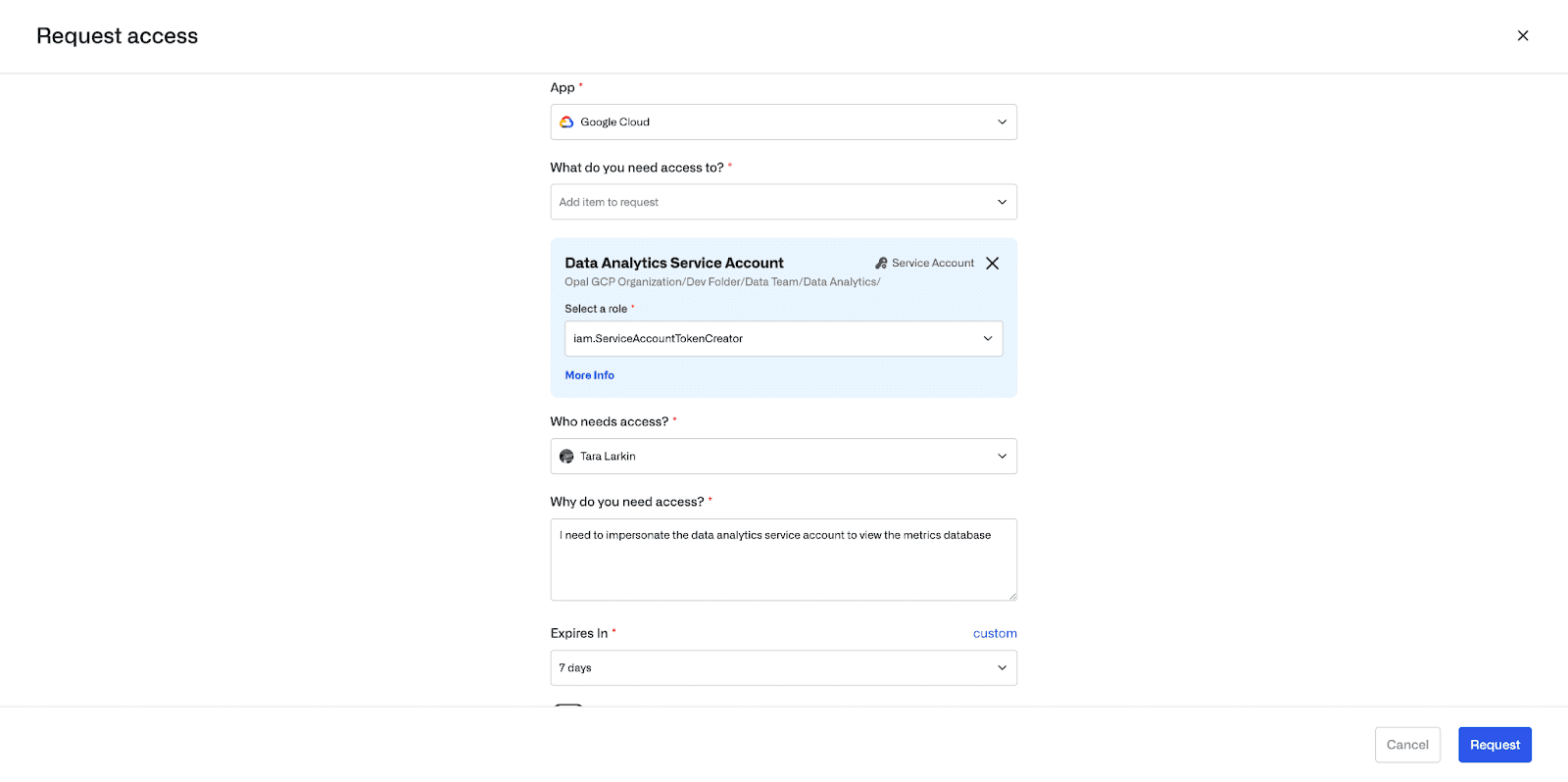
Admins can similarly view all resources that a Service Account has access to. Here we see that the Service Account has access to the Chronicle Service Agent role on the Bigquery Dataset, which it has also inherited onto all of the Dataset’s tables. We can also see that permanent access has been directly granted to the Service Account on the Events table.
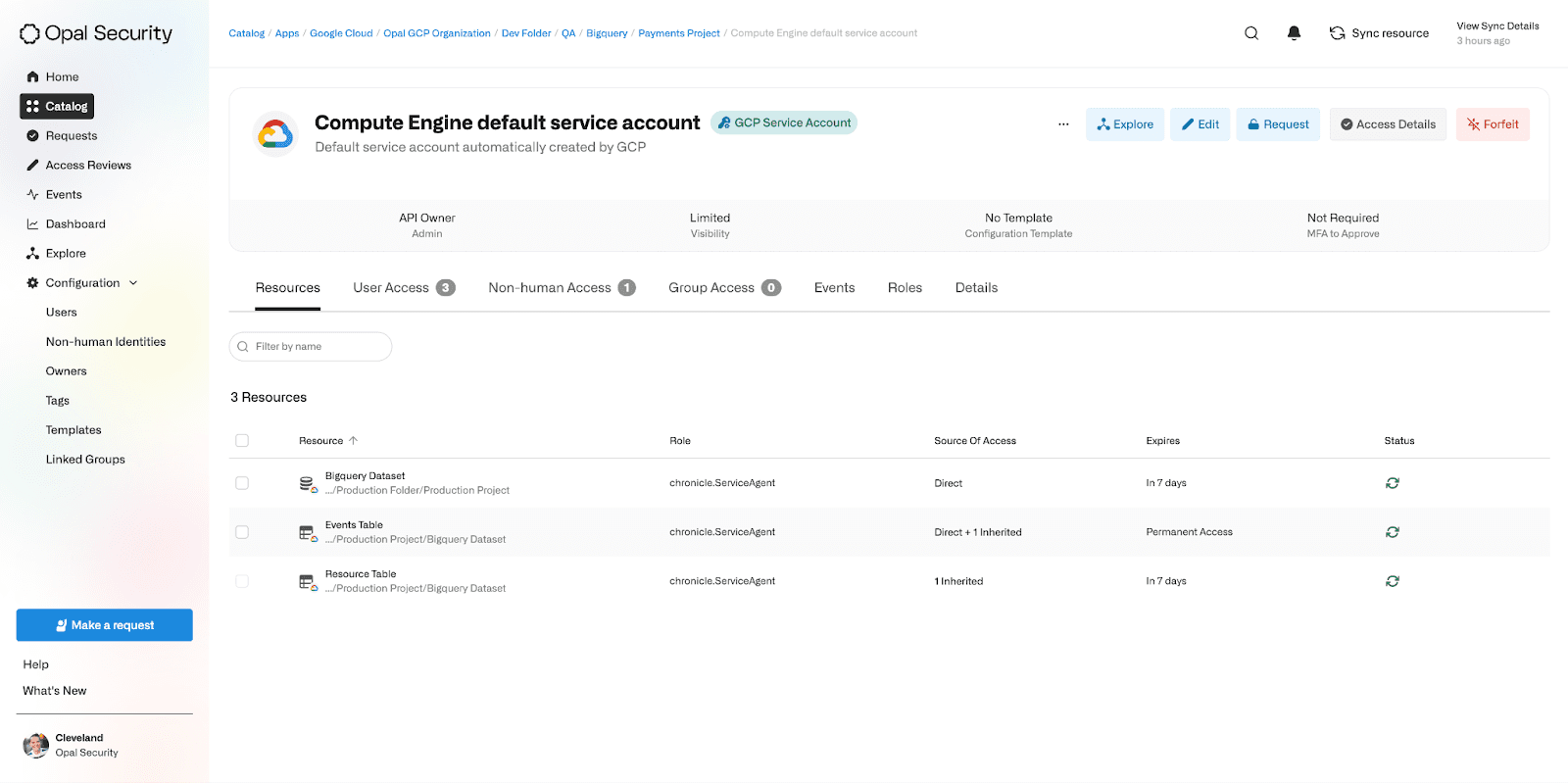
Admins can also view all the Service Accounts that have access to a given GCP resource. These Service Account assignments will be automatically detected and synced into Opal.
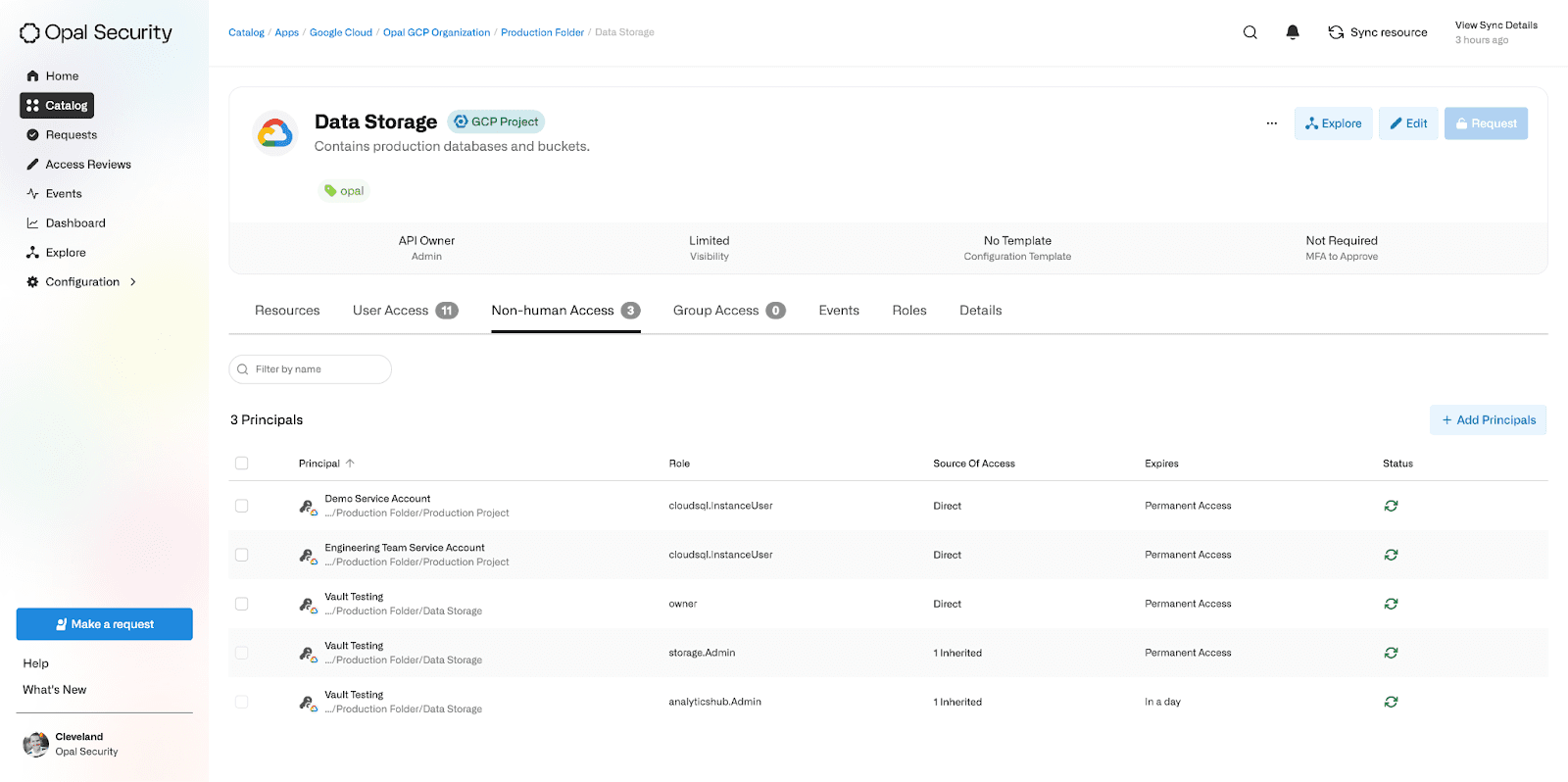
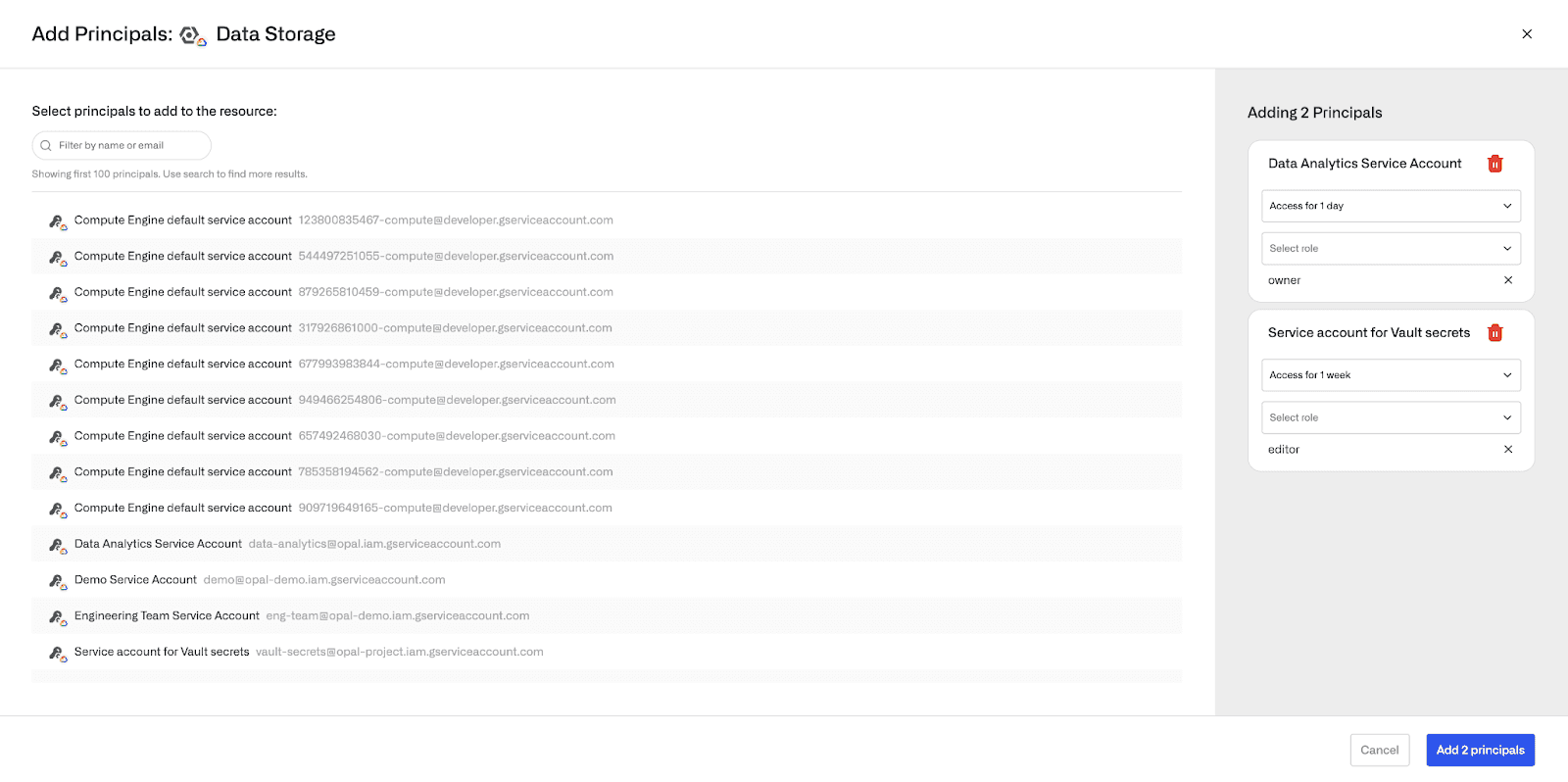
Admins can also add and remove these assignments using Opal. For example, below we are granting the Data Analytics Service Account JIT access to the Owner role on this project. All of these direct assignments can be easily revoked through the non-human access list.
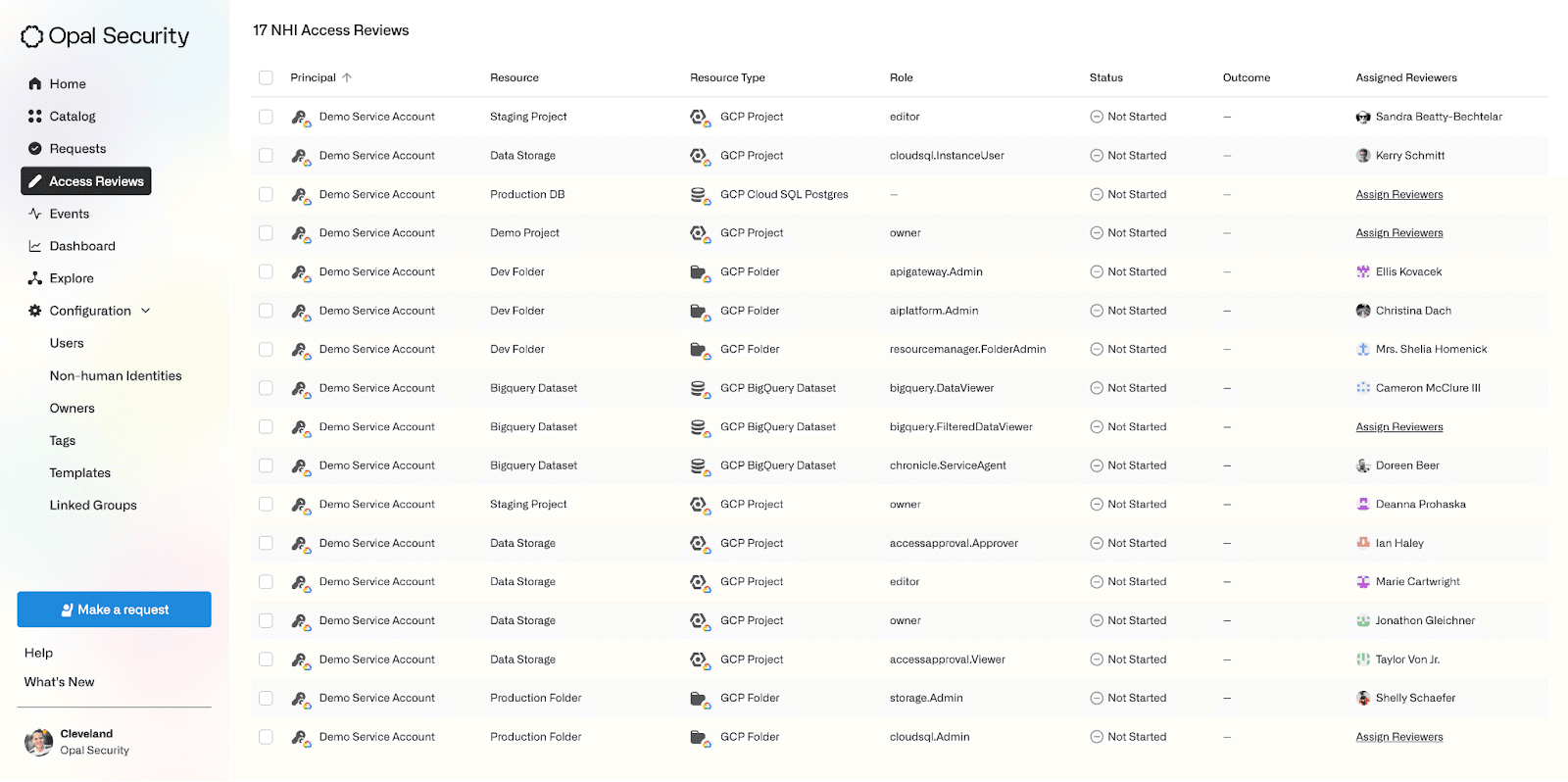
Soon, admins will also have the ability to review Service Account access as a part of Access Reviews! Similar to User Access Reviews, admins can assign reviewers to Service Account assignments and track their review progress as a whole.
How to Import GCP Service Accounts
GCP Service Accounts feature is available in beta for all Opal Security customers. Interested customers can contact their Technical Account Manager to enable this feature.
In order to begin importing Service Accounts into Opal, you will need to update your Opal Service Account’s Role to have the following permissions:
iam.serviceAccounts.get
iam.serviceAccounts.getIamPolicy
iam.serviceAccounts.list
iam.serviceAccounts.setIamPolicy
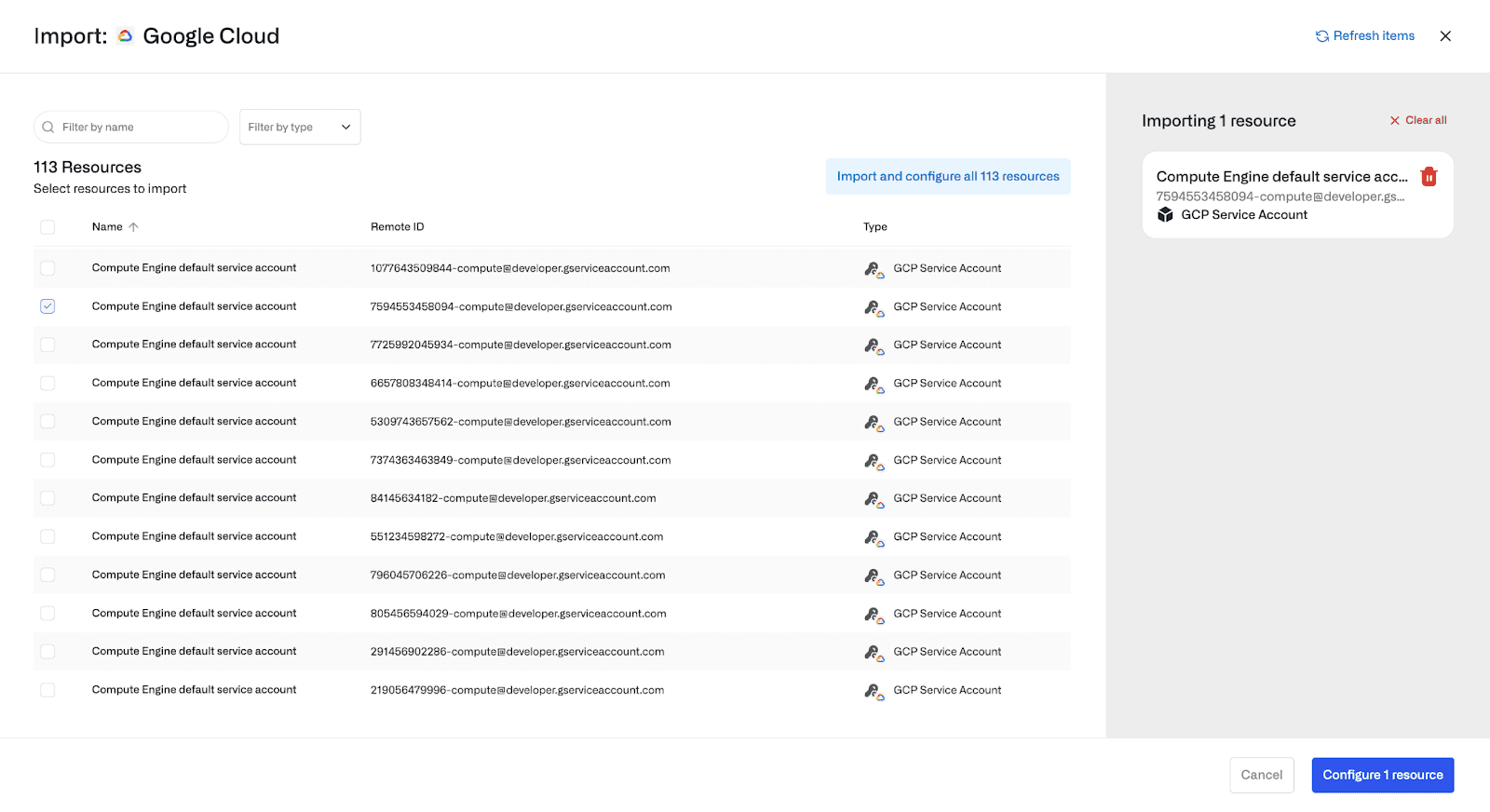
Service Accounts that have access to your resources will be automatically imported into Opal as children of their associated GCP projects. Admins can also select additional Service Accounts to manually import into Opal:
About Opal Security
Opal Security is redefining identity security for modern enterprises. The unified platform aggregates identity and access data to provide customers with visibility and rapid control to protect mission-critical systems while accommodating the complexity and agility businesses require for growth. IT and security teams can discover anomalous identity risks and remediate them in minutes. Many global leaders, including Databricks, Figma and Scale AI, trust Opal Security to enable them to govern and adapt sensitive access quickly and securely.

